Ensto: Bridging Identity Federation Across Enterprise Ecosystems
How Ensto Complements Your Federated IAM Architecture to Secure Multi-Domain Identities
Executive Summary for CISOs
The modern enterprise has become a constellation of identity sources. Your workforce identities originate from corporate directories, while vendors bring their own credentials, partners integrate via federated systems, and clients access your applications through their own identity providers. This distributed identity ecosystem—spanning AWS, Azure, Ping, Okta, Microsoft Entra ID, and countless SaaS applications—creates profound security and compliance challenges.
The core problem isn’t your IAM platform. It’s what happens to identity data after authentication.
Your federation server (whether AWS IAM Identity Center, Ping Identity, or Azure Entra ID) excels at one thing: authentication and authorisation. It verifies “who you are” and “what you can access.” But it was never designed to protect the actual identity data itself once it enters your SaaS applications, data stores, and network infrastructure. That’s where Ensto enters the architecture.
Ensto is not a replacement for your IAM. Instead, it’s a complementary data protection layer that works downstream of your federation infrastructure. By fragmenting, encrypting, and distributing identity data across 25,000+ encrypted storage combinations, Ensto eliminates the single largest vulnerability in federated environments: identity data duplication and exposure.
Part 1: Understanding Federation and the Identity Data Problem
What Is Federated Identity Management?
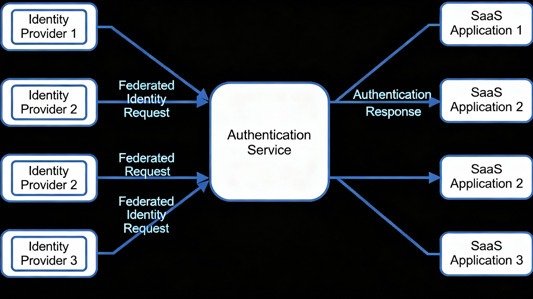
Federated identity management enables organisations to establish trust relationships with external identity providers so users authenticated in one system can access resources in another without managing separate credentials. Instead of storing credentials locally, you trust an external Identity Provider (IdP) to verify “who the user is,” and the application (Service Provider) grants access based on that trust.
The primary protocols enabling federation are SAML 2.0 (used in enterprise for 20+ years), OpenID Connect (modern, OAuth-based), and OAuth 2.0 (authorisation framework). When a user attempts to access a federated resource:
- The application redirects to your federation server
- Your federation server may redirect to an external IdP (if it’s a partner or vendor)
- The IdP authenticates the user
- The IdP returns identity attributes in a signed assertion or token
- Your federation server creates a session
- The user accesses the application
Here’s the critical issue: Once the application receives identity attributes (name, email, department, phone), it stores this data in its database. That identity data is now duplicated in:
- The application’s user database
- Application audit logs
- Your SIEM system’s ingested logs
- Backup systems
- Third-party analytics tools connected to the app
- Potentially dozens of other systems
The Duplication Problem at Scale
Research shows 60% of enterprises experience identity data duplication across SaaS applications. Consider a mid-size enterprise:
- 500 internal employees (federated via Azure Entra ID)
- 200 active vendors (federated via various IdPs)
- 300+ partner users (federated through partner organisations)
- 15 primary SaaS applications (CRM, HR, Finance, Collaboration, etc.)
Each application stores identity data: name, email, department, phone, manager, and custom attributes. If 1,050 total users are active across 15 applications, that’s 15,750 identity records scattered across your infrastructure. In a breach, this multiplied exposure is catastrophic.
Compliance Impact: GDPR requires data minimisation. Storing the same identity in 15 locations is indefensible. CCPA gives users the right to deletion—if identity is duplicated across 15 systems, you must delete from all 15. Gaps create violations.
Breach Impact: In a SaaS compromise, attackers find 15,750 records instead of 1,050. Notification costs multiply by 15x. Regulatory fines escalate. Customer trust erodes exponentially.
Part 2: How Federation Systems Work Today

Architecture Pattern: Hub-and-Spoke Model
Most enterprises use hub-and-spoke architecture, where a central IdP connects to multiple applications. AWS IAM Identity Center acts as a hub connecting to AWS accounts, Salesforce, ServiceNow, and partner systems. Ping Identity serves as a hub for organizations with complex attribute mapping and policy requirements. Azure Entra ID acts as both a hub (for the internal workforce) and connects to B2B partners.
In this architecture, federation servers handle authentication, authorisation policy, and attribute enrichment. When a user authenticates through federation, the server returns signed SAML assertions or OIDC tokens containing identity attributes. Applications receive these attributes and persist them to databases.
Example Flow: A vendor from a partner organisation needs Salesforce access. They authenticate through their company’s Okta instance, which trusts your federation server via SAML. Your federation server creates a session, and Salesforce receives a SAML assertion with the vendor’s name, email, department, and custom attributes. Salesforce stores this data in its user database, logs, and audit systems. Now this vendor’s identity exists in your federation server, Salesforce’s database, Salesforce’s logs, your SIEM, and potentially dozens of other systems.
The vulnerability: Federation protocols (SAML, OIDC, OAuth) were designed for authentication and authorization—not for protecting identity data after authentication. They solve “how do we trust each other?” not “how do we protect the data we’re trusting?”
Part 3: Ensto’s Role as a Data Protection Layer
What Ensto Actually Is (And Isn’t)
Ensto is NOT:
- A replacement for your IAM/federation system
- An authorisation engine
Ensto IS:
- A data protection layer for identity information
- A PII tokenisation platform
- A cryptographic identity security system
- An application-centric identity governance tool
- An enterprise communication tool
Ensto operates downstream of your federation. After your IdP authenticates a user and issues a session token, Ensto transforms identity data through three steps:
- Fragmentation: Identity attributes are split into meaningless fragments (name split and separated from email, separated from phone, separated from department)
- Encryption: Each fragment is encrypted using best-in-class encryption
- Distribution: Encrypted fragments are dispersed across 25,000+ databases and fragmentation combinations
The result: Applications receive identity tokens instead of actual PII. These tokens are non-exploitable—if stolen, they’re meaningless without the fragmentation key stored in Ensto’s infrastructure.
Integration Architecture: AWS IAM Identity Center + Ensto
Your AWS environment uses IAM Identity Center as the federation hub. Corporate directory feeds into it, and it connects to AWS accounts and federated SaaS applications.
Without Ensto: Identity attributes flow from IAM Identity Center to applications, which store them directly in databases.
When Salesforce, ServiceNow, or Slack authenticate users, they receive tokens. Applications store tokens, not identity data. If any application is breached, attackers find only cryptographically unintelligible tokens.
Integration Architecture: Ping Identity + Ping
Ping Identity manages authentication policies, attribute mapping, and creates SAML assertions for applications.
With Ensto Integration:
text
- Identity Sources → Ping Identity → Ensto Middleware → Applications
- (Corporate, Partners, (Authenticates, (Tokenizes (Store tokens
- Vendors) Maps attributes) identity) not PII)
Ping handles what it’s designed for: authentication and policy. Ensto handles what Ping can’t: protecting identity data at the application layer.
Integration Architecture: Azure Entra ID B2B
For organisations with multi-tenant scenarios where customers federate their own Azure Entra ID and vendors use their own IdPs, Ensto provides unified protection.
With Ensto:
text
- Customer 1 Entra ID → Your Entra ID → Ensto → Applications store tokens
- Customer 2 Entra ID → Your Entra ID → Ensto → Applications store tokens
- Vendor Okta → Your Entra ID → Ensto → Applications store tokens
Regardless of the federation source, all identity data flows through Ensto for tokenisation before reaching applications.
Part 4: The Breach Mathematics
Scenario Without Ensto: Salesforce Compromise
Attackers gain database access to Salesforce through a vulnerable API endpoint. They extract user records:
- 1,050 individuals across all federated sources
- Names, emails, departments, phone numbers, managers
- 15,750 total records (counting duplication across apps)
- Regulatory notification required for 1,050 people
- Breach notification cost: $150-$250 per record = $157,500-$262,500
- GDPR fines: Up to 4% of global revenue or €20M
- Customer/partner trust erosion
- Vendor relationship damage
Scenario With Ensto: Same Compromise
Attackers gain the same database access and extract records:
- 5,000 records containing only identity tokens: token_a1b2c3d4, token_e5f6g7h8, etc.
- Tokens are non-exploitable without Ensto’s fragmentation and encryption keys
- Even with database admin access, attackers cannot retrieve underlying identity data
- Regulatory notification: 0 individuals actually impacted (tokens have no exploitable value)
- Breach notification cost: Minimal or zero
- GDPR compliance: Demonstrable data protection
- Customer/partner communications: Enhanced confidence
Part 5: Multi-Domain Federated Identity Scenarios
Real-World Example: Financial Services Firm
A financial services organisation federates identity across multiple domains:
- 5,000 internal employees (Azure Entra ID)
- 200 partner organisations (each with their own IdP: Okta, Ping, Azure AD)
- 500 enterprise customers (federating their own IdPs)
- 20 critical SaaS applications (Salesforce, Workday, Bloomberg, ServiceNow, etc.)
- Regulatory requirements: SOC 2 Type II, FINRA, PCI-DSS, GDPR
Challenge Without Ensto: 7,000 total users × 20 applications = 140,000 identity records. FINRA auditors require access logs. Compliance auditors ask about data minimisation. Identity data governance becomes a nightmare.
With Ensto: All 7,000 users are tokenised regardless of federation source. Applications store only tokens. Audit trails reference tokens, not personal information. Data minimisation is demonstrable. When regulators ask “what identity data is stored in Salesforce?”, the answer is “only application-specific tokens.” Compliance becomes manageable.
Multi-Cloud Federation: AWS + Azure + GCP
Organisations with multi-cloud infrastructure face identity fragmentation across three cloud providers, each with its own identity system:
- AWS IAM (with IAM Identity Center for federation)
- Azure Entra ID (with B2B federation)
- GCP Workload Identity Federation
Without Ensto, identity is synced to each cloud separately, creating duplication and sync challenges. With Ensto, a single identity tokenization layer serves all three clouds. Tokens are issued once, used everywhere, while actual identity data remains protected in Ensto’s infrastructure.
Part 6: Technical Integration and API Design
API Middleware Pattern (Recommended)
For most organisations, Ensto integrates as an API middleware layer between federation and applications:
text
- Application receives federated identity → Ensto API middleware
- → Tokenizes identity → Application stores token
Advantages: Minimal application changes, transparent to federation, standardised approach across all applications.
Implementation: Applications call Ensto APIs to create tokens when users authenticate and retrieve identity data when needed. Fields are requested granularly (request only the data you need, not everything).
Application-Level Integration
For highly sensitive applications (finance, healthcare, legal), Ensto can be embedded directly in the application:
python
- # Application never stores raw identity
- from ensto_sdk import IdentityTokenizer
- tokenizer = IdentityTokenizer(api_key=‘key’, endpoint=‘ensto-api’)
- # When user logs in via federation
- token = tokenizer.create_token(
- user_email=federated_email,
- user_name=federated_name,
- organization=org_id
- )
- # Store only the token in session
- session[‘user_token’] = token
- # When application needs user email
- email = tokenizer.retrieve(token, ’email’)
Advantage: Strongest data protection—applications never store raw identity data.
Part 7: Defending Against Breach Scenarios
Application Database Compromise
Attack: Attacker gains Salesforce database access.
Without Ensto: Attacker finds 5,000 user records with names, emails, departments, phone numbers. They identify high-value targets, perform targeted phishing, correlate with public information.
With Ensto: Attacker finds 5,000 tokens. Tokens are meaningless without Ensto’s distributed fragmentation keys and encryption keys (which aren’t stored in the database). Attackers extract nothing of value.
Application Logs Compromise
Attack: Attacker exfiltrates application logs via a misconfigured S3 bucket.
Without Ensto: Logs contain embedded identity information:
text
- User john.smith@company.com accessed Opportunity ID OP-98765
- User sarah.jones@company.com approved quote for Account ID ACC-54321
With Ensto: Logs reference only tokens:
text
- User token_a1b2c3d4 accessed Opportunity ID OP-98765
- User token_e5f6g7h8 approved quote for Account ID ACC-54321
Attackers cannot determine which real individuals these tokens represent.
Part 8: Compliance and Regulatory Advantages
GDPR Compliance
Article 32 (Data Protection by Design): Ensto demonstrates data protection by design through tokenisation, encryption, and access controls.
Article 17 (Right to Erasure): When users request data deletion, query Ensto for all tokens issued to that user, issue a single deletion command, and all encrypted fragments are destroyed. Compliance evidence shows complete deletion within required timeframes.
CCPA/CPRA
Data Minimisation: Applications store only tokens, not PII. Audit evidence clearly shows that unnecessary identity data isn’t being retained.
Right to Know: When users request “what data do you have about me?”, query Ensto for their tokens across all applications and provide a comprehensive report without touching individual SaaS applications.
SOC 2 Type II
Auditors examine security controls for protecting customer data. Ensto demonstrates:
- Encryption at rest (AES-256)
- Encryption in transit (TLS 1.3)
- Access controls (token-based, application-scoped)
- Comprehensive audit logging
FedRAMP
FedRAMP requires explicit PII encryption, audit logging, and access controls—exactly what Ensto provides.
Part 9: Operational Deployment
Deployment Models
Ensto Cloud (SaaS): Ensto hosts fragmentation, encryption, and distributed storage. Your applications connect to Ensto API endpoints. Best for most organisations—minimal operational overhead.
Ensto Enterprise (Self-Hosted): You deploy Ensto infrastructure in your own data centers or VPCs for organisations with strict data residency requirements or air-gapped infrastructure.
Hybrid: Internal user identity tokenisation in self-hosted Ensto; partner/vendor identity tokenisation in Ensto Cloud. Separates internal and external identity processing.
Integration Timeline
- Months 1-2: Pilot with one application (e.g., Salesforce)
- Months 3-4: Expand to 2-3 critical applications
- Months 5-8: Full deployment across the application portfolio
- Month 8+: Optimisation and policy adjustment
Key Metrics
- Tokenisation Coverage: Percentage of identity data now tokenised (goal: 100%)
- Breach Impact Reduction: Post-deployment breaches expose zero PII
- Audit Efficiency: Compliance audit time should decrease due to data minimisation
Part 10: Advanced Scenarios
API-to-API Federation (Microservices)
In microservices architectures, services authenticate each other using JWTs. With Ensto:
text
- Service A receives user request → Tokenizes identity
- → Service A calls Service B passing token (not user email/name)
- → Service B calls Service C passing token
- → Service C calls Ensto API to retrieve identity if needed
Identity data doesn’t flow through your entire service mesh—only tokens do.
Federated Audit Trails
For compliance audits requiring proof of partner access control:
Without Ensto: Manually search logs for partner user emails, correlate with access, and document findings.
With Ensto: Query Ensto for all tokens issued for organisation X, search audit logs for activity by those tokens, and generate a compliance report automatically.
Part 11: Migration and Best Practices
Greenfield Approach
For new applications, design from the start to use Ensto tokens instead of raw identity. No migration needed—fastest path to compliance.
Gradual Overlay
For existing applications:
- Deploy Ensto API middleware
- Intercept identity data before it reaches application databases
- Write both raw data and tokens initially (parallel operations)
- Migrate existing data to tokenised format in the background
- Switch applications to tokens exclusively
- Archive old raw identity data
Timeline: 4-8 weeks per application, depending on scale.
Success Factors
- Get stakeholder alignment (security, compliance, application teams)
- Define clear success metrics
- Train application teams on token-based identity
- Have rollback procedures (rarely needed)
- Test performance (Ensto adds minimal latency)
Part 12: The Future
Identity Evolution
Identity architecture is evolving from centralised systems (today) toward privacy-first, decentralised models (future). Ensto represents a bridge between current federated systems and future architecture where users own cryptographic credentials.
Federation servers will continue to authenticate users. But alongside them, privacy protection layers (like Ensto) will become mandatory. Organisations implementing Ensto today are building the infrastructure for tomorrow’s identity landscape.
Conclusion
For CISOs, the message is clear: Authentication and authorisation are necessary but insufficient for modern identity security.
Your federation systems excel at verifying “who you are” and “what you can access.” They don’t protect identity data once it enters your applications and databases.
Ensto complements federation architecture by providing a unified data protection layer. Regardless of which IdP authenticated a user (corporate, partner, vendor, customer), Ensto ensures identity data is tokenised, fragmented, encrypted, and distributed.
In the event of a breach, identity data remains protected by multiple layers. Attackers find tokens, fragments, and encryption—not exploitable personal information.
For your organisation:
- Reduced breach notification scope: Compromised systems contain only tokens
- Simpler compliance: Data minimisation requirements are clearly met
- Better partnerships: You can assure partners that their employees’ data is protected
- Future-proof architecture: You’re building infrastructure for zero-trust, privacy-first systems
The question isn’t whether to adopt identity data protection—it’s when. As breaches accelerate and regulations tighten, federated environments without explicit identity protection become indefensible.
Ensto makes identity data protection simple, transparent, and integrated with existing federation architecture. No IAM rip-and-replace needed. Just add protection where it matters most: your identity data.