Beyond Access: The New Standard for Identity Security in Financial Services
Why enabling Ensto over Okta is the paradigm shift your CISOs have been waiting for
Explore the future of identity security in finance services with advanced verification, seamless access, and stronger customer trust.
Executive Summary: The “Identity Anxiety” of Modern Finance
In the high-stakes world of financial services, trust is the currency of record. Yet, that currency is being devalued at an alarming rate. We are living through an era of “Identity Anxiety,” where 75% of users avoid signups due to data concerns and 60% reject data exchanges entirely. For a financial institution, this isn’t just a marketing hurdle; it is an existential threat.
For the last decade, the industry’s response to this threat has been centralised Access Management. We locked the front doors. We bought best-in-class solutions like Okta to ensure that only the right people could enter our digital buildings. And Okta has done a phenomenal job—it is the gold standard for Single Sign-On (SSO) and Multi-Factor Authentication (MFA).
But here is the uncomfortable truth: Locking the front door doesn’t help if the valuables are left scattered on the front lawn.
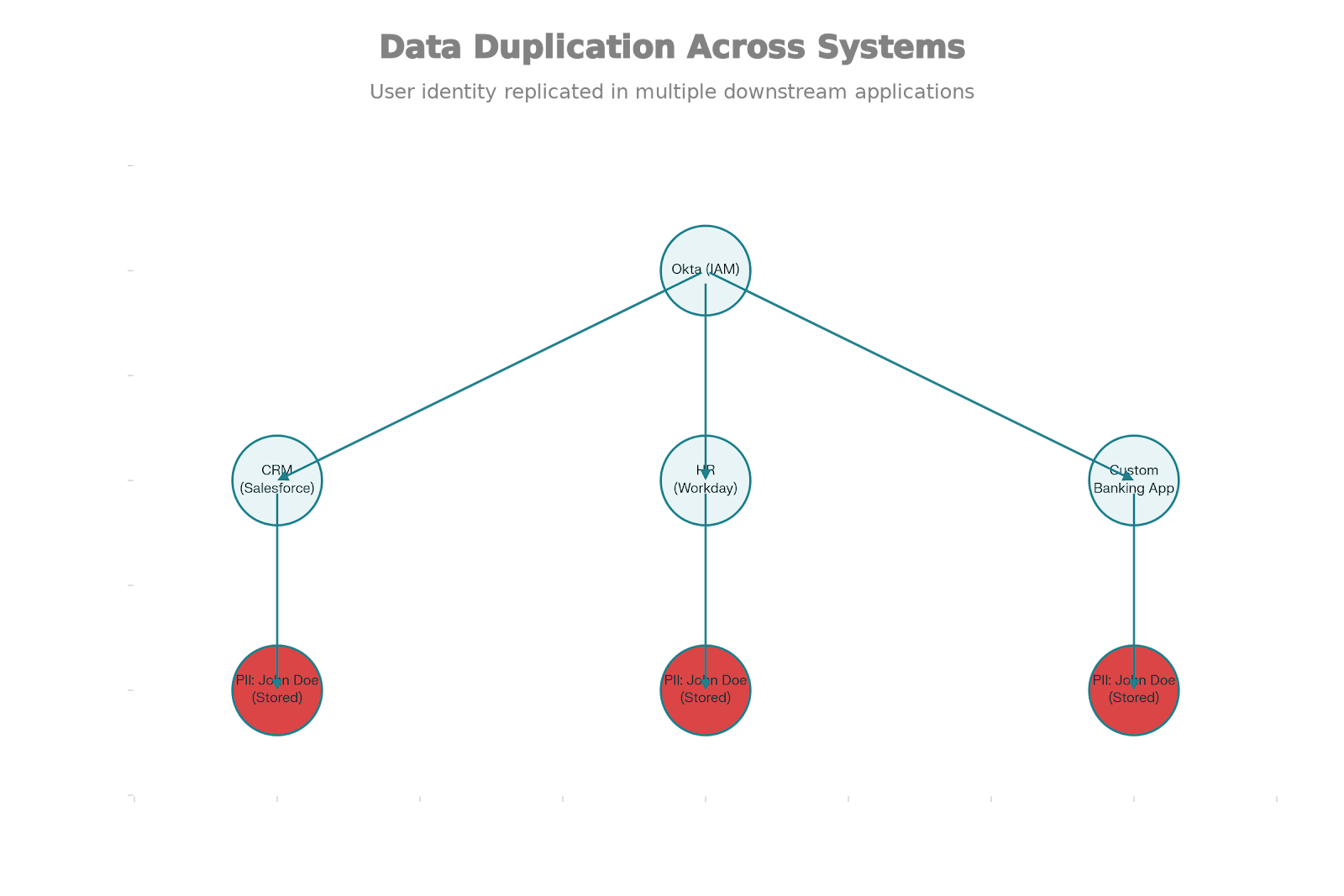
In the modern financial enterprise, identity data is not sitting in a secure vault; it is duplicated, fragmented, and exposed across hundreds of SaaS applications. Your CRM, your HR system, your marketing automation platform, and your legacy on-prem core banking system—all of them hold redundant copies of your customers’ Personally Identifiable Information (PII). This is the “Data Duplication” crisis, and it is the single biggest liability facing FinTech today.
This report outlines a new architectural approach: layering Ensto’s Identity(AI) Platform over your existing Okta infrastructure. It is a strategy that moves us from merely managing access to fundamentally protecting identity.
Part 1: The Status Quo — The “Spiderweb” of Risk
To understand the solution, we must first honestly assess the problem. Let’s look at a representative financial institution: FinCorp Global.
FinCorp relies on Okta as its Identity and Access Management (IAM) provider. This was a smart investment. Okta centralises authentication, enforces robust MFA policies, and streamlines user provisioning. When a FinCorp employee, “Sophie West,” logs in to check client portfolios, Okta verifies she is who she says she is.
However, once Okta opens the door, its job is largely done. It hands Sophie over to the application—be it Salesforce, Workday, or a custom loan origination app. To function, these applications believe they need to own the data. So, during the provisioning process, Okta (or a manual process) pushes Sophie’s PII—her name, email, role, and perhaps even sensitive client details—directly into the databases of these SaaS providers.
This creates a “Spiderweb of Risk.”
The Multiplier Effect of Duplication
If FinCorp uses 100 SaaS applications (a conservative estimate for a bank), they likely have 100 copies of Sophie’s identity profile stored in 100 different databases, managed by 100 different security teams with varying levels of competence.
- The Attack Surface: An attacker doesn’t need to breach FinCorp’s robust Okta perimeter. They just need to breach one of the 100 downstream vendors.
- The Consequence: If the HR platform is compromised, Sophie’s data is stolen. It doesn’t matter that FinCorp had MFA enabled; the data was sitting at rest in a third-party database.
- The Stat: Enterprises now incur an average of $4 million+ per data breach, with 95% of Fortune 1000 companies seeing their user records exposed.
Part 2: Enter Ensto — “Applications Over Information”
If Okta is the Bouncer (checking IDs at the door), Ensto is the Vault (ensuring there’s nothing to steal if someone sneaks in).
Ensto represents a shift to Identity 2.5, bridging the gap between centralised corporate directories and decentralised privacy-first identity. Its core philosophy is simple yet revolutionary: “Applications over Information.” Applications should perform logic; they should not hoard identity data.
The Technology: Fragmentation, Encryption, Distribution
Ensto solves the duplication crisis through a patent-pending process that renders data unintelligible to attackers. When an identity is created or ingested by Ensto:
- Fragmentation: The data (e.g., “Sophie West”) is broken down into meaningless fragments.
- Encryption: Each fragment is encrypted using best-in-class cryptography.
- Distribution: These encrypted fragments are intelligently dispersed across 25,000+ database and collection combinations.
The Result: Unintelligible Data
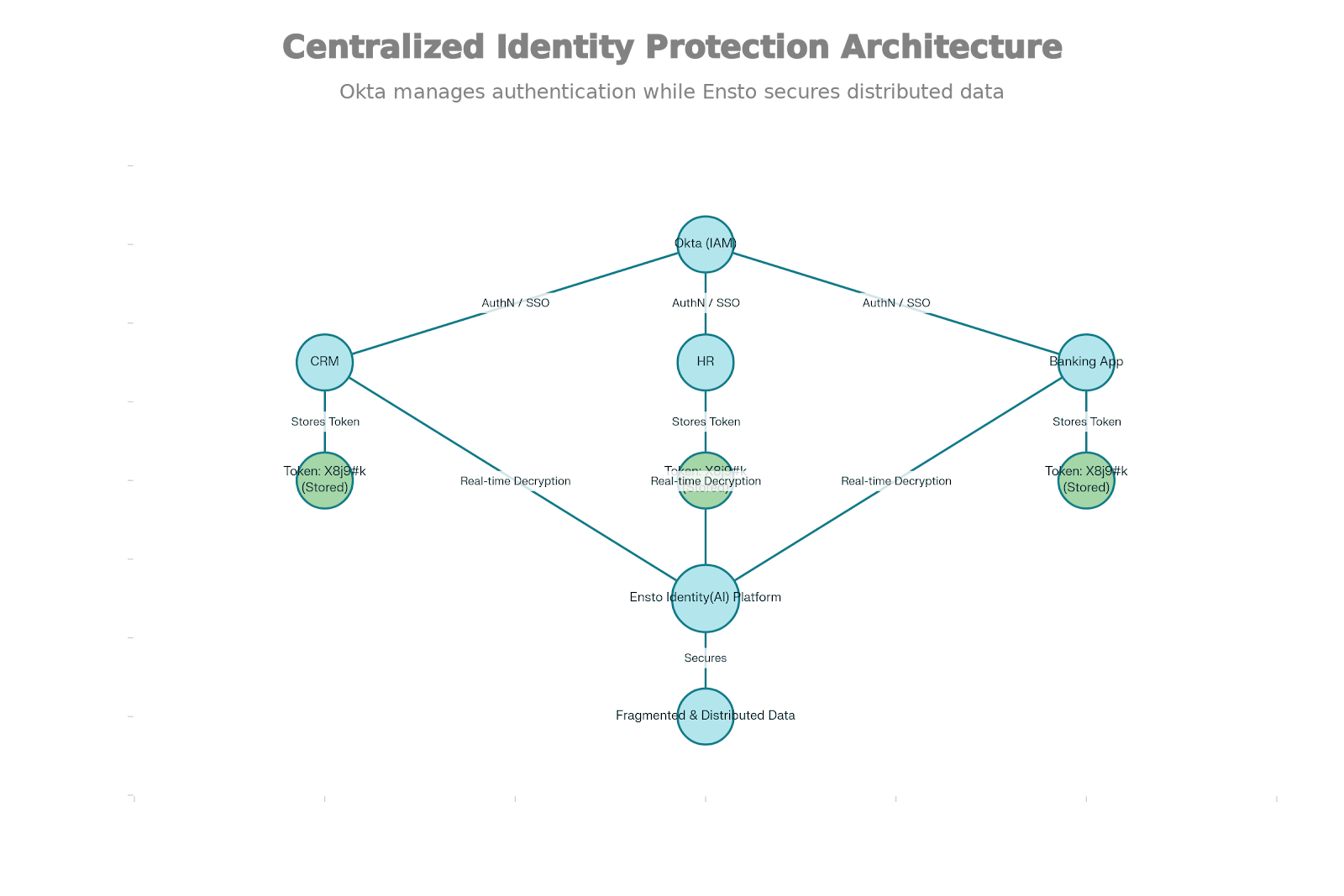
In an Ensto-enabled environment, the SaaS application does not store “Sophie West.” It stores an Identity Token.
If a cybercriminal breaches the SaaS CRM database, they find a table full of useless alphanumeric strings. They cannot reverse-engineer the original data because they lack the reassembly logic and the decryption keys, which are held securely within the Ensto platform. Even if they breach the Ensto platform itself, the data is so heavily fragmented and distributed that exfiltrating a meaningful record is practically impossible.
Key Differentiator: While IAMs like Okta encrypt data at rest, they typically store the encrypted blob in a single location that, if decrypted with a stolen key, reveals the full record. Ensto’s fragmentation means there is no single “record” to steal.
Part 3: The Integration Strategy — Enabling Ensto Over Okta
For a financial services company, “ripping and replacing” core infrastructure is rarely an option. The power of Ensto lies in its ability to complement Okta, not replace it.
Here is the step-by-step architectural workflow for enabling Ensto within an Okta-centric environment.
Phase 1: The “Identity Audit” (Discovery)
Before implementation, the FinCorp security team must map the flow of PII.
- Action: Audit the Okta Universal Directory and identifying which attributes are being pushed to downstream apps via SCIM (System for Cross-domain Identity Management).
- Goal: Identify high-risk SaaS apps that are storing sensitive PII purely for display or minor logic purposes.
Phase 2: Tokenization & The “Ensto APIs”
This is the enablement phase. Instead of provisioning raw string data (e.g., user.lastName = “West”), the architecture changes to provision Ensto Tokens.
- The Connector: Ensto provides API integrations that sit between the Identity Source and the Service.
- The Shift: When a new user is created in Okta (or mastered in HR and imported to Okta), Ensto intercepts the PII creation event.
- Ensto fragments and stores the real data.
- Ensto returns a unique Identity Token to Okta.
- The Push: Okta now pushes this Token to Salesforce, Slack, and the Core Banking App instead of the PII.
Phase 3: The Runtime Workflow (The “Better Together” Flow)
How does the application work if it doesn’t have the data? This is where the runtime integration shines.
- Authentication (Okta): Sophie logs into the Banking Portal. Okta handles the SAML/OIDC flow, verifying her credentials and MFA or using Ensto’s authentication forms. This can remain unchanged.
- Authorization (Okta): Okta grants Sophie an access token for the portal.
- Data Retrieval (Ensto): The Banking Portal loads. It sees Sophie’s UserID is associated with Token_ABC123.
- Scenario A (Display): The Portal needs to display “Welcome, Sophie.” It makes a real-time, secure API call to Ensto with the token. Ensto reassembles the fragments, decrypts them, and returns the name “Sophie” ephemerally. The browser displays it, but the database never writes it to disk.
- Scenario B (Communication): The Portal needs to send Sophie an email. Instead of retrieving her email address, the Portal asks Ensto’s Communication Service to “Send Template X to Token_ABC123.” Ensto resolves the email internally and sends the message. The Portal never sees or stores the email address.
Part 4: Comparative Analysis — Why You Need Both
Financial executives often ask, “Doesn’t Okta already do this?” The answer is nuanced. Okta is an Access tool; Ensto is a Privacy tool. They solve different layers of the OSI model of identity.
| Feature | Okta (IAM) | Ensto (Identity AI) | The Combined Value |
| Primary Function | Authentication & Authorisation (Who are you?) | Data Protection & Privacy (What do we know about you?) | Verified users accessing protected data. |
| Data at Rest | Encrypted (usually centralised) | Unintelligible (Fragmented & Encrypted & Distributed) | If the IAM is breached, the data is still safe. |
| Data Duplication | High (Pushes data to apps) | Zero (Tokens replace data) | Eliminates the downstream attack surface. |
| SaaS PII Storage | Relies on SaaS vendor’s security | Eliminated (SaaS holds tokens) | Vendor breaches no longer compromise your clients. |
| Cyber Resilience | High (for access control) | Extreme (Data is useless to thieves) | Breaches become “non-events” (no data to ransom). |
The ROI of “No Data Stolen”
Consider the scenario where a major SaaS CRM used by FinCorp is hacked (a supply chain attack).
- With just Okta: The attackers dump the database. They get names, emails, phone numbers, and account statuses. FinCorp must declare a breach, pay fines, and suffer reputational damage.
- With Okta + Ensto: The attackers dump the database. They find millions of tokens like 8f92-ka29-b102. They cannot use them. They cannot ransom them. FinCorp revokes the tokens and reissues new ones. Zero data exfiltration. Zero regulatory fine. Zero trust lost.
Part 5: Implementation Guide for the Financial CIO
Implementing Ensto over Okta is a strategic initiative that can be executed in phases to minimise disruption.
Phase 1: Pilot with High-Risk Internal Apps (Months 1-3)
Start with custom internal applications (e.g., an internal advisor dashboard). These are easiest to control because you own the code.
- Configure Ensto platform: Modify the dashboard to accept and store tokens.
- Configure Okta: Set up a custom attribute mapping in Okta to pass the Ensto Token instead of the raw PII for this specific app.
- Test: Verify that the dashboard can still display user details by calling Ensto APIs at runtime.
Phase 2: The “Communication” Shift (Months 4-6)
Financial services generate massive amounts of email and SMS traffic (OTPs, statements, alerts).
- Migrate Logic: Move email sending logic from individual SaaS apps to the Ensto Communication interface.
- Purge: Once verified, purge the email address columns from your downstream marketing automation databases, replacing them with tokens.
Phase 3: SaaS Vendor Integration (Months 6-12)
For closed-source SaaS (like Salesforce), use Ensto’s proxy or gateway capabilities (or work with Ensto’s growing ecosystem of pre-built integrations).
- Gateway Approach: Route traffic through an Ensto Gateway that tokenizes PII on the fly before it hits the SaaS API.
- Field-Level Encryption: Use SaaS “Shield” encryption features where the key management is offloaded to Ensto.
Conclusion: The Future is “Zero Knowledge”
The financial services industry is approaching a tipping point. The old model of “copying data everywhere and trying to defend it everywhere” is mathematically impossible to sustain. The attack surface is simply too large.
By layering Ensto over Okta, FinCorp moves to a “Zero Knowledge” architecture. The applications that power the business no longer need to know who the customer is—they only need to know how to serve them.
- Okta ensures that only Sophie West can log in.
- Ensto ensures that Sophie West’s data effectively doesn’t exist on the network until the exact millisecond it is needed, and vanishes the moment it is not.
This isn’t just a security upgrade; it is a restoration of the digital trust that banking was built on. In a world of inevitable breaches, the only safe data is data that isn’t there.



