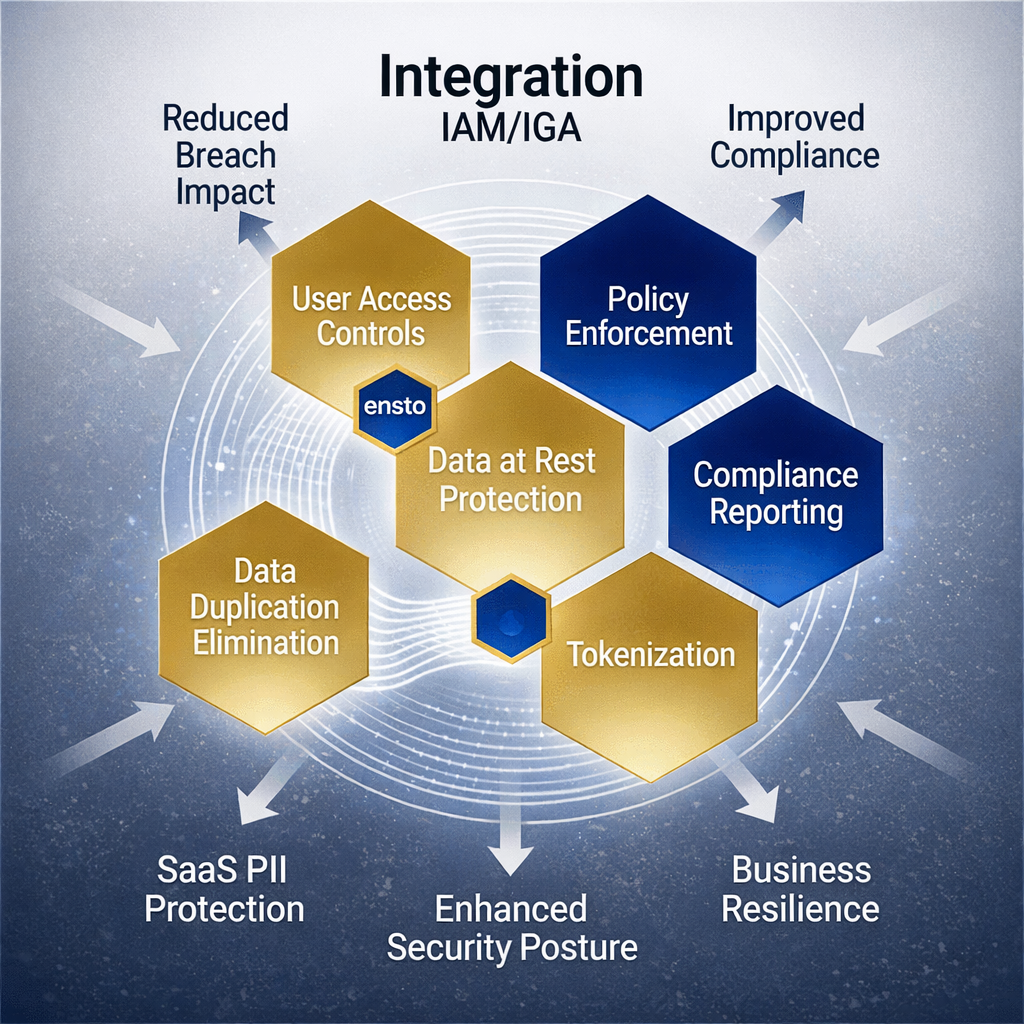
Why Your Identity Governance Programme is Incomplete Without Ensto: The Identity Golden Record Enterprise Need
Identity Governance Administration (IGA) has long been the cornerstone of enterprise identity management, yet most organisations remain fundamentally exposed. Despite implementing sophisticated IGA platforms, IT executives face a critical blind spot: traditional IGAs solve policy and access administration beautifully, but leave the actual identity data—the crown jewels—vulnerable to the very threats it’s designed to prevent. This gap represents a hidden architectural vulnerability that compounds every time identity data duplicates across your SaaS ecosystem.
The IGA Paradox: Governance Without Data Security
Modern IGA solutions excel at what they were built for: managing who accesses what, enforcing policies, and maintaining audit trails. They orchestrate access across hybrid environments, automate provisioning workflows, and ensure compliance reporting. However, this orchestration requirement creates a fundamental problem. IGA platforms must maintain centralised, readable identity records to manage access effectively. This centralisation—the very thing that makes governance possible—becomes a high-value target for attackers. Enterprise SaaS applications compound this exposure by duplicating identity data across their systems. Research indicates that 60% of enterprise SaaS applications maintain duplicate identity records, creating a fragmented landscape where the same identity record exists in multiple discoverable formats across your infrastructure.
The economics are stark. When attackers breach an IGA-protected environment, they don’t encounter policy constraints—they encounter readable identity records. What you’ve actually built is a single point of failure dressed in governance clothing. Your IGA platform has made managing access efficient, but it hasn’t addressed what attackers truly seek: data. Across Fortune 1000 companies, 95% have reported data leaks in cyberattacks over the past decade, yet most IGA deployments still treat identity data protection as a secondary concern, subordinate to access control orchestration.
Enter Ensto: The Identity Golden Record
Ensto fundamentally reframes identity governance by introducing a security layer that traditional IGA cannot provide: an unintelligible identity golden record. Unlike conventional IAM repositories that store identity data in encrypted but readable formats, Ensto uses patent-pending fragmentation technology to break identity data into meaningless, distributed pieces that exist across 25,000+ database combinations. This isn’t encryption in the traditional sense—it’s architectural unintelligibility. Even with administrative access to your infrastructure, attackers find no coherent identity records to extract.
For IT executives responsible for enterprise risk, this distinction is critical. Ensto operates as a complementary identity layer that preserves everything your IGA platform does—policy management, role administration, access certification, compliance workflows—while adding the security architecture your IGA cannot deliver. Your IGA continues to manage access decisions and governance policies. Ensto manages what IGA cannot: making identity data structurally incapable of being stolen or duplicated in meaningful form.
How Ensto Transforms Identity Governance Effectiveness
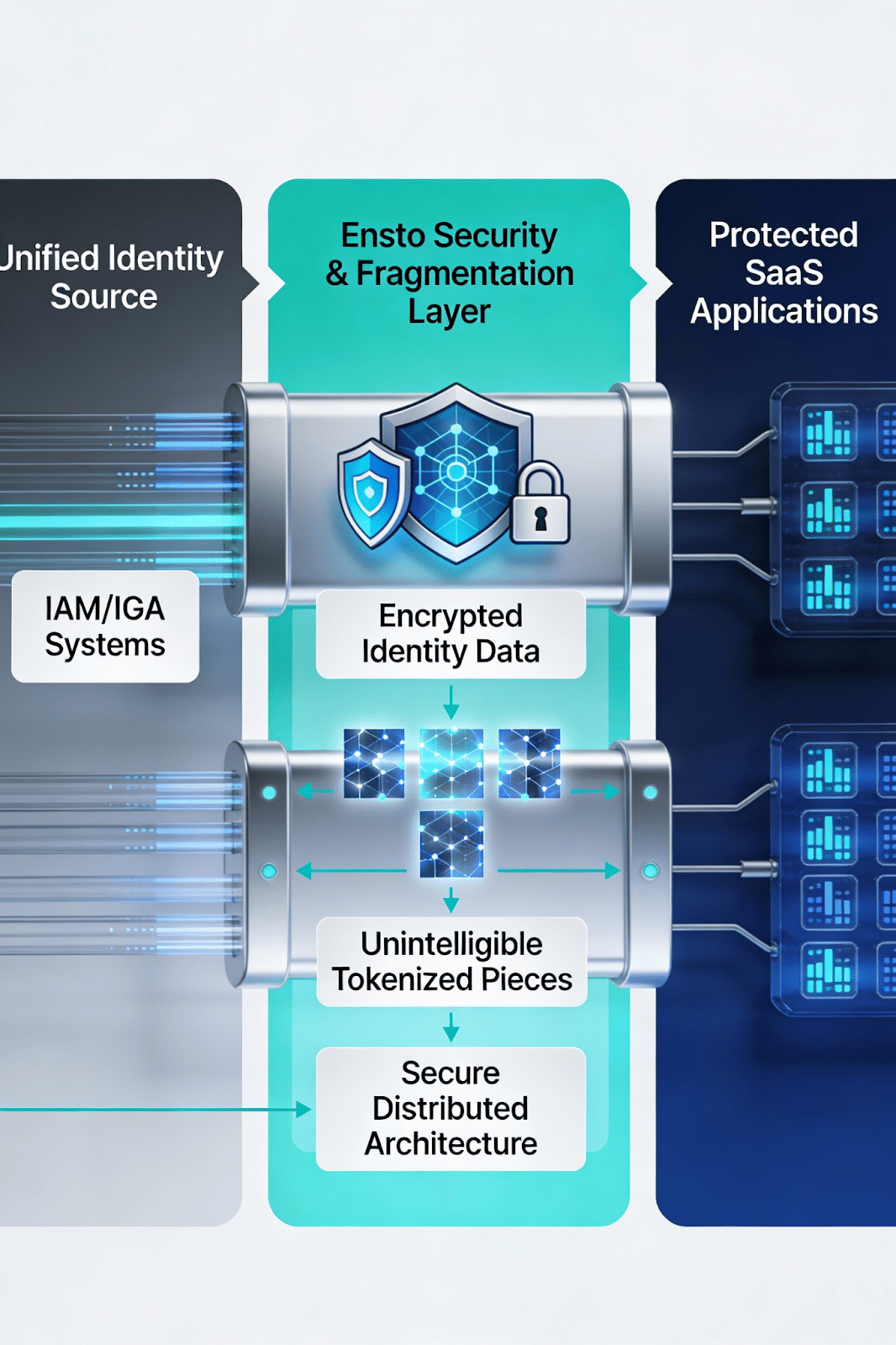
The integration of Ensto into your IGA architecture creates a three-tier identity security model:
First tier: IGA policy orchestration. Your existing IGA platform makes access decisions, manages roles, enforces policies, and maintains governance records. This remains unchanged and optimized.
Second tier: Ensto identity protection. Before identity data reaches your SaaS applications, Ensto intercepts it, fragments it into unintelligible pieces, and encrypts each fragment with cryptographic keys managed across distributed systems. Identity data never exists in complete, readable form within your applications. SaaS applications receive secure identity tokens instead of actual user data. This eliminates data duplication at the source—if your applications never store complete identity records, they have nothing to duplicate.
Third tier: Enterprise SaaS applications. Your applications continue operating normally, but they work with tokenized identity instead of PII. From the application’s perspective, they have the identity information they need for authentication and authorization. From a security perspective, they’ve been relieved of the liability of storing sensitive identity data.
The Data Duplication Problem Solved
Traditional IGA struggles with a fundamental architectural problem: the more systems you govern, the more places identity records must exist, and the more duplication occurs. Each system requires some form of identity data to function. This creates an exponential expansion of attack surface. A Fortune 500 company might have identity records in HR systems, enterprise directories, CRM platforms, marketing automation tools, ITSM platforms, and dozens of SaaS applications. That same person’s identity exists in potentially 50+ locations, each storing similar but slightly different data, creating maintenance nightmares and security exposure.
Ensto eliminates this duplication mathematically. When SaaS applications never store actual identity data—only tokens—the duplication problem ceases to exist at the point where attackers currently find the most value. Your IGA platform still maintains its authoritative identity source, but that source is now the only location where complete identity records exist. Every other system in your architecture works with fragmented, tokenized information that has no intelligence value if exfiltrated.
The Flexibility and Resilience Imperative
Modern enterprises require identity governance that adapts to hybrid, multi-cloud, and increasingly decentralized environments. Traditional IGA provides flexibility in policy administration but remains rigid in its core vulnerability: centralized, readable identity data. Ensto provides the architectural flexibility IGA cannot achieve independently.
Consider a breach scenario. With traditional IGA, a successful attack means data loss—identity records must be restored, customers notified, and regulatory processes initiated. With Ensto protecting your identity layer, a successful attack means attackers find encrypted, fragmented data they cannot weaponize. Your IGA-managed access controls remain intact. Your identity tokens can be reissued. Your applications continue operating. This isn’t damage control; it’s true cyber resilience.
From an implementation perspective, Ensto integrates seamlessly with your existing IGA infrastructure. Your IAM platform (whether Okta, Entra ID, Ping, Sailpoint, or others) continues doing what it was designed for. Ensto adds a security layer that was never part of the original IAM/IGA value proposition. This layered approach means IT teams can implement identity enhancement without wholesale platform replacement.
Compliance and Audit Considerations
IGA deployments often struggle with a persistent challenge: demonstrating to auditors and regulators that identity data is truly protected. Encrypted data in readable format still carries risk. Zero-trust architectures acknowledge this truth—data should be unintelligible, not just encrypted. Ensto aligns with modern zero-trust frameworks by ensuring that even with system access, identity data remains structurally protected.
For compliance officers and IT security leaders, this translates to simpler audit narratives. Rather than explaining encryption key management at scale, you can demonstrate that identity data exists in fragmented, unintelligible form distributed across multiple systems. Regulatory frameworks increasingly expect this architectural approach, particularly for sensitive PII and identity data. GDPR and emerging privacy regulations emphasize data minimization and structural protection—principles Ensto directly addresses through its fragmentation architecture.
Implementation Realities
Organizations implementing Ensto alongside their existing IGA platforms report significant operational improvements. The fragmentation and distribution of identity data requires computation, but Ensto’s patent-pending technology processes this at scale with latencies acceptable for enterprise environments. Most deployments maintain sub-100ms identity validation times, which IGA platforms and applications handle transparently.
From a developer perspective, the integration becomes an architectural decision, not a technical burden. APIs accept identity tokens instead of raw identity data. Applications store nothing but token references. This simplifies compliance for application teams, reduces their security liability, and accelerates development cycles by removing the requirement to handle sensitive identity data securely.
The Path Forward
Your IGA platform will continue doing exactly what it was designed for—governance, administration, and orchestration. But IGA was never designed to make identity data unintelligible to attackers. That’s a fundamentally different architectural problem, and it requires a fundamentally different solution.
For IT executives responsible for enterprise risk, the question isn’t whether to replace your IGA platform. The question is whether you can afford to continue operating an identity governance programme that manages access brilliantly but leaves your actual identity data vulnerable to the theft and duplication that continues to drive breach costs upward.
Ensto doesn’t replace your IGA. It completes it. By adding architectural protection that IGA cannot provide—unintelligible, distributed identity records and enterprise-scale tokenization—Ensto transforms identity governance from a policy-based access control framework into a comprehensive identity protection architecture. Your compliance officers will have clarity on data protection. Your security teams will have resilience your current architecture cannot deliver. Your IT operations will have efficiency gains through simplified identity management across your SaaS ecosystem.
The future of identity governance isn’t IGA alone. It’s IGA enhanced with the architectural protection that only a platform purpose-built for identity fragmentation and unintelligibility can provide.