For years, encryption has been the security world’s favourite comfort blanket. Encrypt the data. Lock it down. Sleep better at night. But here’s the uncomfortable truth most enterprises are now facing: encrypted data still gets breached, misused, and exploited—every single day. If encryption were enough, breach headlines would be a thing of the past. They aren’t. And that tells us something important. Let’s talk about why encryption alone no longer cuts it, and why making data unintelligible by design is becoming the next big shift in identity and data security. The Encryption Comfort Myth: Beyond the False Sense of Security For decades, encryption has been the “gold standard” of the security playbook—a mathematical shield that feels impenetrable. When organizations encrypt data at rest and in transit, they often check a box and assume the job is done. However, this confidence is increasingly misplaced as attackers evolve beyond trying to “break” the math. The “Harvest Now, Decrypt Later” (HNDL) Threat The old assumption was that encrypted data is useless to a thief. That is no longer true. We are now seeing the rise of Harvest Now, Decrypt Later. State actors and sophisticated hacking groups are proactively exfiltrating massive amounts of encrypted data today, even if they can’t read it yet. They are banking on the future: as quantum computing advances, the encryption protocols of today will likely fall, allowing them to unlock years of historical secrets retroactively. Why Encryption Isn’t a Cloaking Device Even when your data remains “unbreakable,” encryption does not make it invisible. Modern attackers use Traffic Analysis and Metadata Profiling to bypass the shield: Database Mapping: Even without the keys, hackers can analyze encrypted database blobs to determine the exact number of user records, the frequency of updates, and the size of the dataset. This allows them to value their “haul” before they even crack it. The Vulnerability of Use: Data must be decrypted to be processed. This “moment of use” is the primary target for memory scraping and side-channel attacks. Architectural Leaks: Encryption often hides the content but reveals the context. An attacker can see that a high-volume encrypted stream is heading to a specific payroll API, identifying exactly where the most valuable assets live. The Reality Check Encryption is a necessary layer, but it isn’t a vault. It’s a delay tactic. If your security strategy ends at encryption, you aren’t protecting your data—you’re just archiving it for a future breach. The SaaS Sprawl: Multiplication of the Attack Surface While “Harvest Now, Decrypt Later” targets the data itself, SaaS Sprawl targets the infrastructure. In a modern enterprise, PII is rarely isolated. It is synchronized, exported, and duplicated across a web of interconnected platforms—from CRM systems and marketing automation tools to “productivity” plugins and shadow IT apps. Every time a user connects a third-party app to your core environment, they aren’t just granting access; they are often creating a “Shadow Data” duplicate. A hacker doesn’t need to breach your heavily fortified core database if they can find one less secure, niche application with a “read-all” permission. This is the Weakest Link Strategy: attackers look for the smallest, least-managed app in your ecosystem that contains a synced copy of your user records. Once that app is compromised, they can exfiltrate the same high-value PII as if they had hit the main server, often without triggering the primary system’s alarms. The PII Visibility Gap Even if your primary systems are locked down, duplication creates a visibility gap that hackers exploit: Credential Lateral Movement: A breach in a small, third-party tool often yields valid user emails and metadata that can be used for highly targeted phishing or credential stuffing against your main environment. Shadow Data Persistence: When an employee leaves or a project ends, the data in niche apps often remains. These “toxic logs” and abandoned databases become sitting ducks for attackers. The “Mirror” Effect: Many integrations require a full mirror of your user list to function. This means your attack surface isn’t just one system. The Reality: In a SaaS-heavy world, your security is only as strong as the most obscure app your marketing team signed up for during a free trial. Real-world breaches where encryption didn’t save the day Look at major breaches over the last decade. In many cases, attackers didn’t break encryption. They simply logged in. Stolen credentials. Misconfigured access. Overprivileged accounts. The data was encrypted right up until it was handed over, nicely decrypted, to someone who shouldn’t have seen it. Encryption wasn’t broken. Trust was. What Encryption Actually Solves—and What It Doesn’t Encryption protects data at rest and in transit To be clear, encryption is essential. It prevents raw data from being read if storage is stolen or traffic is intercepted. That’s table stakes. No serious security strategy skips this step. But encryption solves a very specific problem, not the whole problem. Who can still read the data once decrypted Once decrypted, the data is readable by: Applications Administrators APIs Third-party tools Anyone with valid (or stolen) access At that point, encryption steps aside. If access controls fail—and they often do—your most sensitive data becomes instantly usable. Insider threats and compromised credentials Not all threat actors wear black hoodies. Disgruntled employees, careless insiders, or attackers using stolen credentials don’t need to hack anything. They just walk through the front door. Encryption doesn’t stop them. It was never designed to. The illusion of safety once keys and access exist Encryption keys, access tokens, and permissions create a fragile trust chain. Break one link, and the entire system is exposed. That’s why relying solely on encryption creates an illusion of safety—one that disappears the moment access is abused. The Real Problem: Readable Data Everywhere Data duplication across SaaS apps and platforms Modern enterprises love SaaS. CRM here. HR tools there. Collaboration apps everywhere. But each tool often stores its own copy of user data. Same PII. Multiple places. Multiple risks. More copies mean more attack surfaces.
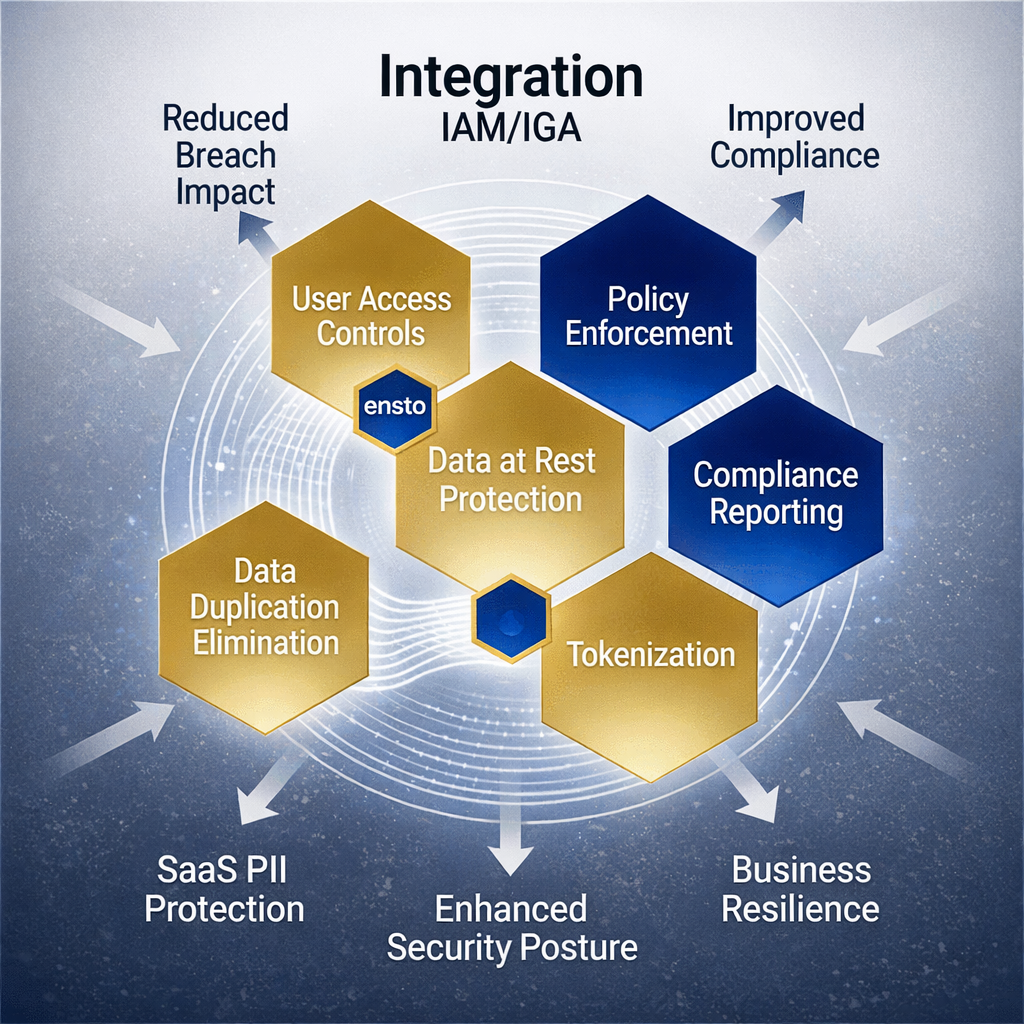
Identity Governance Administration (IGA) has long been the cornerstone of enterprise identity management, yet most organisations remain fundamentally exposed. Despite implementing sophisticated IGA platforms, IT executives face a critical blind spot: traditional IGAs solve policy and access administration beautifully, but leave the actual identity data—the crown jewels—vulnerable to the very threats it’s designed to prevent. This gap represents a hidden architectural vulnerability that compounds every time identity data duplicates across your SaaS ecosystem. The IGA Paradox: Governance Without Data Security Modern IGA solutions excel at what they were built for: managing who accesses what, enforcing policies, and maintaining audit trails. They orchestrate access across hybrid environments, automate provisioning workflows, and ensure compliance reporting. However, this orchestration requirement creates a fundamental problem. IGA platforms must maintain centralised, readable identity records to manage access effectively. This centralisation—the very thing that makes governance possible—becomes a high-value target for attackers. Enterprise SaaS applications compound this exposure by duplicating identity data across their systems. Research indicates that 60% of enterprise SaaS applications maintain duplicate identity records, creating a fragmented landscape where the same identity record exists in multiple discoverable formats across your infrastructure. The economics are stark. When attackers breach an IGA-protected environment, they don’t encounter policy constraints—they encounter readable identity records. What you’ve actually built is a single point of failure dressed in governance clothing. Your IGA platform has made managing access efficient, but it hasn’t addressed what attackers truly seek: data. Across Fortune 1000 companies, 95% have reported data leaks in cyberattacks over the past decade, yet most IGA deployments still treat identity data protection as a secondary concern, subordinate to access control orchestration. Enter Ensto: The Identity Golden Record Ensto fundamentally reframes identity governance by introducing a security layer that traditional IGA cannot provide: an unintelligible identity golden record. Unlike conventional IAM repositories that store identity data in encrypted but readable formats, Ensto uses patent-pending fragmentation technology to break identity data into meaningless, distributed pieces that exist across 25,000+ database combinations. This isn’t encryption in the traditional sense—it’s architectural unintelligibility. Even with administrative access to your infrastructure, attackers find no coherent identity records to extract. For IT executives responsible for enterprise risk, this distinction is critical. Ensto operates as a complementary identity layer that preserves everything your IGA platform does—policy management, role administration, access certification, compliance workflows—while adding the security architecture your IGA cannot deliver. Your IGA continues to manage access decisions and governance policies. Ensto manages what IGA cannot: making identity data structurally incapable of being stolen or duplicated in meaningful form. How Ensto Transforms Identity Governance Effectiveness The integration of Ensto into your IGA architecture creates a three-tier identity security model: First tier: IGA policy orchestration. Your existing IGA platform makes access decisions, manages roles, enforces policies, and maintains governance records. This remains unchanged and optimized. Second tier: Ensto identity protection. Before identity data reaches your SaaS applications, Ensto intercepts it, fragments it into unintelligible pieces, and encrypts each fragment with cryptographic keys managed across distributed systems. Identity data never exists in complete, readable form within your applications. SaaS applications receive secure identity tokens instead of actual user data. This eliminates data duplication at the source—if your applications never store complete identity records, they have nothing to duplicate. Third tier: Enterprise SaaS applications. Your applications continue operating normally, but they work with tokenized identity instead of PII. From the application’s perspective, they have the identity information they need for authentication and authorization. From a security perspective, they’ve been relieved of the liability of storing sensitive identity data. The Data Duplication Problem Solved Traditional IGA struggles with a fundamental architectural problem: the more systems you govern, the more places identity records must exist, and the more duplication occurs. Each system requires some form of identity data to function. This creates an exponential expansion of attack surface. A Fortune 500 company might have identity records in HR systems, enterprise directories, CRM platforms, marketing automation tools, ITSM platforms, and dozens of SaaS applications. That same person’s identity exists in potentially 50+ locations, each storing similar but slightly different data, creating maintenance nightmares and security exposure. Ensto eliminates this duplication mathematically. When SaaS applications never store actual identity data—only tokens—the duplication problem ceases to exist at the point where attackers currently find the most value. Your IGA platform still maintains its authoritative identity source, but that source is now the only location where complete identity records exist. Every other system in your architecture works with fragmented, tokenized information that has no intelligence value if exfiltrated. The Flexibility and Resilience Imperative Modern enterprises require identity governance that adapts to hybrid, multi-cloud, and increasingly decentralized environments. Traditional IGA provides flexibility in policy administration but remains rigid in its core vulnerability: centralized, readable identity data. Ensto provides the architectural flexibility IGA cannot achieve independently. Consider a breach scenario. With traditional IGA, a successful attack means data loss—identity records must be restored, customers notified, and regulatory processes initiated. With Ensto protecting your identity layer, a successful attack means attackers find encrypted, fragmented data they cannot weaponize. Your IGA-managed access controls remain intact. Your identity tokens can be reissued. Your applications continue operating. This isn’t damage control; it’s true cyber resilience. From an implementation perspective, Ensto integrates seamlessly with your existing IGA infrastructure. Your IAM platform (whether Okta, Entra ID, Ping, Sailpoint, or others) continues doing what it was designed for. Ensto adds a security layer that was never part of the original IAM/IGA value proposition. This layered approach means IT teams can implement identity enhancement without wholesale platform replacement. Compliance and Audit Considerations IGA deployments often struggle with a persistent challenge: demonstrating to auditors and regulators that identity data is truly protected. Encrypted data in readable format still carries risk. Zero-trust architectures acknowledge this truth—data should be unintelligible, not just encrypted. Ensto aligns with modern zero-trust frameworks by ensuring that even with system access, identity data remains structurally protected. For compliance officers and IT security leaders, this translates to simpler audit narratives. Rather than explaining encryption key
The Double Burden: Privacy Concerns AND Subscription Fatigue You’re juggling multiple platforms. LinkedIn for credibility. Email for follow-ups. Maybe a digital business card app—another monthly subscription you probably didn’t want. And each time you network, you’re forced into an uncomfortable choice: expose your personal information or miss the opportunity. Here’s what’s really happening: 75% of professionals avoid signing up for networking opportunities citing data concerns. They won’t download your vCard. They won’t click your shared contact link. They’re paralyzed by the fear that sharing their details—phone number, email, location—could lead to spam, identity theft, or worse. Meanwhile, you’re paying for digital business card tools that collect your data just like every other platform, adding another subscription to your growing tech stack. The irony? You’re trying to build relationships, but every tool in your arsenal broadcasts that you’re collecting information. Your prospects see expense, complexity, and privacy risk. You see frustration, stalled pipelines, and wasted budget. For sales and marketing professionals, this creates a painful paradox. You need contact information to nurture leads and build relationships, yet every data request—and every expensive tool you use to request it—signals risk and friction to your prospects. They don’t want another subscription. They don’t want to worry about where their information ends up. And honestly, neither do you. Enter Connecto: Privacy-First Networking Without the Price Tag Stop paying for digital business card apps that don’t respect privacy and don’t respect your wallet. Connecto is built differently. It’s not another online business card platform. It’s a privacy-first communication app that lets you share secure digital contact cards instantly—without exposing your phone number or personal data to unknown contacts. Recipients don’t even need the app to access your card. No friction. No extra logins. No hidden fees. Here’s what changes the game: Hide your real number from unknown contacts. When someone reaches out through Connecto, they can communicate with you without ever seeing your actual phone number. No spam. No unwanted calls. Just genuine business conversations. Share contact cards securely. Instead of asking prospects to fill out forms or download apps, you send them an encrypted digital card. They access it instantly. No data collection on your end. No anxiety on theirs. One tool, multiple uses. Secure messaging, encrypted calls, AI-powered spam blocking, adaptive privacy modes—Connecto does what five separate subscriptions try to do, but built on privacy from the ground up. For sales professionals, this is a relationship accelerator that actually respects boundaries. When a prospect receives a secure contact card from you via Connecto instead of a forwarded email or a hastily written number, they’re experiencing a brand moment. You’re showing them that privacy matters to you—that you’re different from the other platforms demanding their data. That respect translates to trust, and trust translates to deals. Building Trust Through Privacy-Focused Practices The solution isn’t to ask for less information—it’s to ask for information in ways that protect privacy. When prospects trust that their data is genuinely secure and you’re not running another exploitative subscription service, friction disappears and conversions improve. Start by being transparent about what you collect and why. Share your privacy commitments upfront. Most importantly, demonstrate that you respect privacy boundaries. Limit data requests to what you genuinely need. Instead of asking for phone numbers, email addresses, and company details upfront, consider starting with essentials and building that relationship gradually using tools like Connecto that were designed for privacy, not profit extraction. Adjust your platform settings to show prospects you’re serious about privacy. Let them control what they share with you—and with whom in your organization. This transparency builds credibility and reduces the hesitation that kills deals. Tightening Your Digital Security Practices Beyond communication tools, strengthen your core security habits. These protect you and reassure your prospects that you’re a trustworthy partner. Use strong, unique passwords for every account and leverage a password manager to avoid reuse. Enable two-factor authentication (2FA) on all professional accounts—LinkedIn, email, CRM systems. That second verification layer stops attackers even when credentials are compromised. Review connected applications regularly. Apps you authorized a year ago for “LinkedIn integration” or “contact sync” may still have access to sensitive information. Revoke what you don’t actively use. Audit your public digital footprint. Search your name online. What appears? Outdated contact information, old articles, dormant forum profiles? These weak points attract bad actors. Clean them up. Update or remove old profiles. This housekeeping protects your professional reputation and your personal security. Privacy Settings: Non-Negotiable for Pros Your LinkedIn profile, email settings, and cloud apps change their privacy policies constantly. You can’t set them once and forget. Treat privacy configuration as ongoing maintenance. Customize LinkedIn visibility. Control who sees your email, phone, and profile details. Limit your profile visibility to your network or even further. For sales professionals seeking passive inbound leads, stay visible; if you prefer active outreach, tighten it down. Manage app permissions. How many apps can access your contacts, calendar, or location? Periodically audit these permissions and revoke anything unnecessary. Each connection is a potential entry point for your data. Document your sharing practices. When you give a platform access to your data, document what you shared and why. This helps you audit and revoke access later. Turning Data Anxiety Into Competitive Advantage Here’s the insight that changes everything: prospects who trust your privacy practices are more likely to convert into customers and remain loyal. When you demonstrate that you respect their data and actively protect yours, you’re not just reducing risk—you’re building brand differentiation. Sales and marketing professionals who emphasize privacy-first practices stand out. Your messaging shifts from “share your data with us” to “we protect your data and respect your privacy.” That’s a conversation winner. You’re not asking them to trust another subscription service—you’re inviting them into a relationship built on mutual respect. Take Control Today Privacy-focused networking doesn’t mean isolation—it means smarter, more secure engagement. By adopting these practices and leveraging tools like Connecto, you reclaim control over your digital identity and professional relationships without subscription
Why enabling Ensto over Okta is the paradigm shift your CISOs have been waiting for Explore the future of identity security in finance services with advanced verification, seamless access, and stronger customer trust. Executive Summary: The “Identity Anxiety” of Modern Finance In the high-stakes world of financial services, trust is the currency of record. Yet, that currency is being devalued at an alarming rate. We are living through an era of “Identity Anxiety,” where 75% of users avoid signups due to data concerns and 60% reject data exchanges entirely. For a financial institution, this isn’t just a marketing hurdle; it is an existential threat. For the last decade, the industry’s response to this threat has been centralised Access Management. We locked the front doors. We bought best-in-class solutions like Okta to ensure that only the right people could enter our digital buildings. And Okta has done a phenomenal job—it is the gold standard for Single Sign-On (SSO) and Multi-Factor Authentication (MFA). But here is the uncomfortable truth: Locking the front door doesn’t help if the valuables are left scattered on the front lawn. In the modern financial enterprise, identity data is not sitting in a secure vault; it is duplicated, fragmented, and exposed across hundreds of SaaS applications. Your CRM, your HR system, your marketing automation platform, and your legacy on-prem core banking system—all of them hold redundant copies of your customers’ Personally Identifiable Information (PII). This is the “Data Duplication” crisis, and it is the single biggest liability facing FinTech today. This report outlines a new architectural approach: layering Ensto’s Identity(AI) Platform over your existing Okta infrastructure. It is a strategy that moves us from merely managing access to fundamentally protecting identity. Part 1: The Status Quo — The “Spiderweb” of Risk To understand the solution, we must first honestly assess the problem. Let’s look at a representative financial institution: FinCorp Global. FinCorp relies on Okta as its Identity and Access Management (IAM) provider. This was a smart investment. Okta centralises authentication, enforces robust MFA policies, and streamlines user provisioning. When a FinCorp employee, “Sophie West,” logs in to check client portfolios, Okta verifies she is who she says she is. However, once Okta opens the door, its job is largely done. It hands Sophie over to the application—be it Salesforce, Workday, or a custom loan origination app. To function, these applications believe they need to own the data. So, during the provisioning process, Okta (or a manual process) pushes Sophie’s PII—her name, email, role, and perhaps even sensitive client details—directly into the databases of these SaaS providers. This creates a “Spiderweb of Risk.” The Multiplier Effect of Duplication If FinCorp uses 100 SaaS applications (a conservative estimate for a bank), they likely have 100 copies of Sophie’s identity profile stored in 100 different databases, managed by 100 different security teams with varying levels of competence. The Attack Surface: An attacker doesn’t need to breach FinCorp’s robust Okta perimeter. They just need to breach one of the 100 downstream vendors. The Consequence: If the HR platform is compromised, Sophie’s data is stolen. It doesn’t matter that FinCorp had MFA enabled; the data was sitting at rest in a third-party database. The Stat: Enterprises now incur an average of $4 million+ per data breach, with 95% of Fortune 1000 companies seeing their user records exposed. Part 2: Enter Ensto — “Applications Over Information” If Okta is the Bouncer (checking IDs at the door), Ensto is the Vault (ensuring there’s nothing to steal if someone sneaks in). Ensto represents a shift to Identity 2.5, bridging the gap between centralised corporate directories and decentralised privacy-first identity. Its core philosophy is simple yet revolutionary: “Applications over Information.” Applications should perform logic; they should not hoard identity data. The Technology: Fragmentation, Encryption, Distribution Ensto solves the duplication crisis through a patent-pending process that renders data unintelligible to attackers. When an identity is created or ingested by Ensto: Fragmentation: The data (e.g., “Sophie West”) is broken down into meaningless fragments. Encryption: Each fragment is encrypted using best-in-class cryptography. Distribution: These encrypted fragments are intelligently dispersed across 25,000+ database and collection combinations. The Result: Unintelligible Data In an Ensto-enabled environment, the SaaS application does not store “Sophie West.” It stores an Identity Token. If a cybercriminal breaches the SaaS CRM database, they find a table full of useless alphanumeric strings. They cannot reverse-engineer the original data because they lack the reassembly logic and the decryption keys, which are held securely within the Ensto platform. Even if they breach the Ensto platform itself, the data is so heavily fragmented and distributed that exfiltrating a meaningful record is practically impossible. Key Differentiator: While IAMs like Okta encrypt data at rest, they typically store the encrypted blob in a single location that, if decrypted with a stolen key, reveals the full record. Ensto’s fragmentation means there is no single “record” to steal. Part 3: The Integration Strategy — Enabling Ensto Over Okta For a financial services company, “ripping and replacing” core infrastructure is rarely an option. The power of Ensto lies in its ability to complement Okta, not replace it. Here is the step-by-step architectural workflow for enabling Ensto within an Okta-centric environment. Phase 1: The “Identity Audit” (Discovery) Before implementation, the FinCorp security team must map the flow of PII. Action: Audit the Okta Universal Directory and identifying which attributes are being pushed to downstream apps via SCIM (System for Cross-domain Identity Management). Goal: Identify high-risk SaaS apps that are storing sensitive PII purely for display or minor logic purposes. Phase 2: Tokenization & The “Ensto APIs” This is the enablement phase. Instead of provisioning raw string data (e.g., user.lastName = “West”), the architecture changes to provision Ensto Tokens. The Connector: Ensto provides API integrations that sit between the Identity Source and the Service. The Shift: When a new user is created in Okta (or mastered in HR and imported to Okta), Ensto intercepts the PII creation event. Ensto fragments and stores the real data.
We live in a world where you can’t get through the day without contacting strangers. You call delivery drivers to share directions. You text buyers on OLX, Facebook Marketplace, or WhatsApp. You speak with service providers, plumbers, electricians, brokers… the list goes on. It’s normal. It’s necessary. But it’s not always safe. Sharing your personal number with strangers especially in 2025 is like handing out your home keys to random people just because they came to drop a parcel. Your mobile number is tied to your identity, online accounts, financial services, and even your location in many cases. So yes, giving it away casually is risky. The good news? You no longer have to. There’s a smarter, safer way to call or text anyone without revealing your number or risking your privacy. And no, it’s not a burner number. And definitely not those shady apps that “promise” security but harvest your data like a buffet. This smarter way is the Connecto App, a privacy-first communication app that hides your number, protects your identity, and lets you connect freely without compromise. Let’s break down why this matters and how it works. Why You Should Never Share Your Personal Mobile Number A. Privacy Risks Your phone number is a digital fingerprint. Once someone has it, they can: Track your digital identity Scrape your online presence Sell your number to marketing agencies Link your number to social media profiles Access your WhatsApp photo, name, last seen, and activity That’s a lot of free information to give a stranger. B. Safety Risks Your number can be misused in several ways: Spam calls Banking scam attempts Harassment Fake loan calls SIM-jacking attempts Fraud through OTP guessing attacks One wrong person with your number and your peace of mind is gone. C. Reputation Risks Mixing your personal and external interactions leads to: Work contacts calling your personal number Buyers messaging you late at night Delivery agents calling long after the order Strangers saving your number permanently Once your number is out, it’s out forever. Your phone number shouldn’t be your identity it should be your tool. And tools need boundaries. Common “Solutions” People Use And Why They Fail People try different tricks to protect their numbers, but sadly, most of these don’t work. 1. Using a second SIM Sounds smart, but: You still expose a personal number SIM registration still links your identity You get spam on both numbers Carrying two phones is annoying 2. Burner numbers Hollywood made them look cool. Reality? Not so much. Burner apps often store data Many leak call logs Some sell usage data to marketers Most don’t work with OTPs or real services 3. Using WhatsApp/Telegram This is a common mistake. Your number is still visible Your profile photo, name, and online status are exposed People can message you anytime They can forward your number to others 4. Temporary calling apps Most of them are… questionable. Ads everywhere Data stored on unknown servers Poor voice quality Require both users to install the app Charge ridiculous fees So what’s the real problem? These solutions hide your number partially, but they do not hide your identity. And that’s where Connecto changes the entire game. What You Actually Need: A Zero-Identity Communication Layer To communicate safely with strangers in today’s digital world, you need one thing: A communication layer that protects you first. Here’s what a truly safe solution must have: No number sharing No call logs stored anywhere No SMS data stored No metadata tracking No third-party access Works with normal calling and SMS Simple enough for everyday use And that’s exactly why the Connecto App exists. It gives you a zero-identity communication experience meaning you can talk to anyone without giving away anything. How Connecto Lets You Call or Text Strangers Without Revealing Your Number This is where things get interesting. A. How Connecto’s Identity Layer Works Connecto creates a private identity layer between you and the other person. Here’s what it does: Your real number stays completely hidden The app manages your calls and SMS securely No logs are saved—not on servers, not in the cloud No contact details are shared No metadata is stored Only you control what’s visible and what’s not Think of it as a digital invisibility cloak for your number. You call and text normally but only you know your real number. B. Key Features That Make Connecto Private & Powerful Privacy-first calling Private SMS with no data storage Hide your number anytime (default or per call) Smart digital contact cards (no app needed for recipients) End-to-end encryption AI-powered spam blocking Multiple privacy modes (work, personal, incognito) Adaptive AI identity protection You’re basically upgrading your phone to a secure communication hub. C. Why Connecto Is Safer Than Burner Numbers or Regular Phone Apps Most calling apps say they’re safe. Connecto actually proves it. With Connecto: 0 stored data 0 tracking 0 unknown servers 0 metadata leaks 0 contact sharing It works instantly, replaces your default phone/SMS app, and protects you in real time. Real-Life Use Cases: When You Should Use Connecto Let’s get real. You talk to strangers more often than you think. Here are the most common situations where the Connecto App becomes your best friend: 1. Marketplace Platforms (OLX, Quikr, Facebook Marketplace) Buyers and sellers are complete strangers. Don’t give them your real number. Ever. 2. Delivery Agents Sometimes they call continuously. Sometimes they save your number. Not with Connecto. 3. Dating Apps You should never give your number to someone you barely know. With Connecto, you stay safe and anonymous until you decide otherwise. 4. Freelancing or Gig Work Clients shouldn’t have your personal number. Keep your boundaries professional. 5. Service Providers (Electricians, plumbers, carpenters) They don’t need to store your number. Connect safely without exposing your identity. 6. Rental Enquiries (brokers, landlords, tenants) Avoid spam, follow-ups, and harassment. Communicate privately. 7. Customer Support Interactions Don’t give your number to temporary agents or unknown companies. Bottom line:
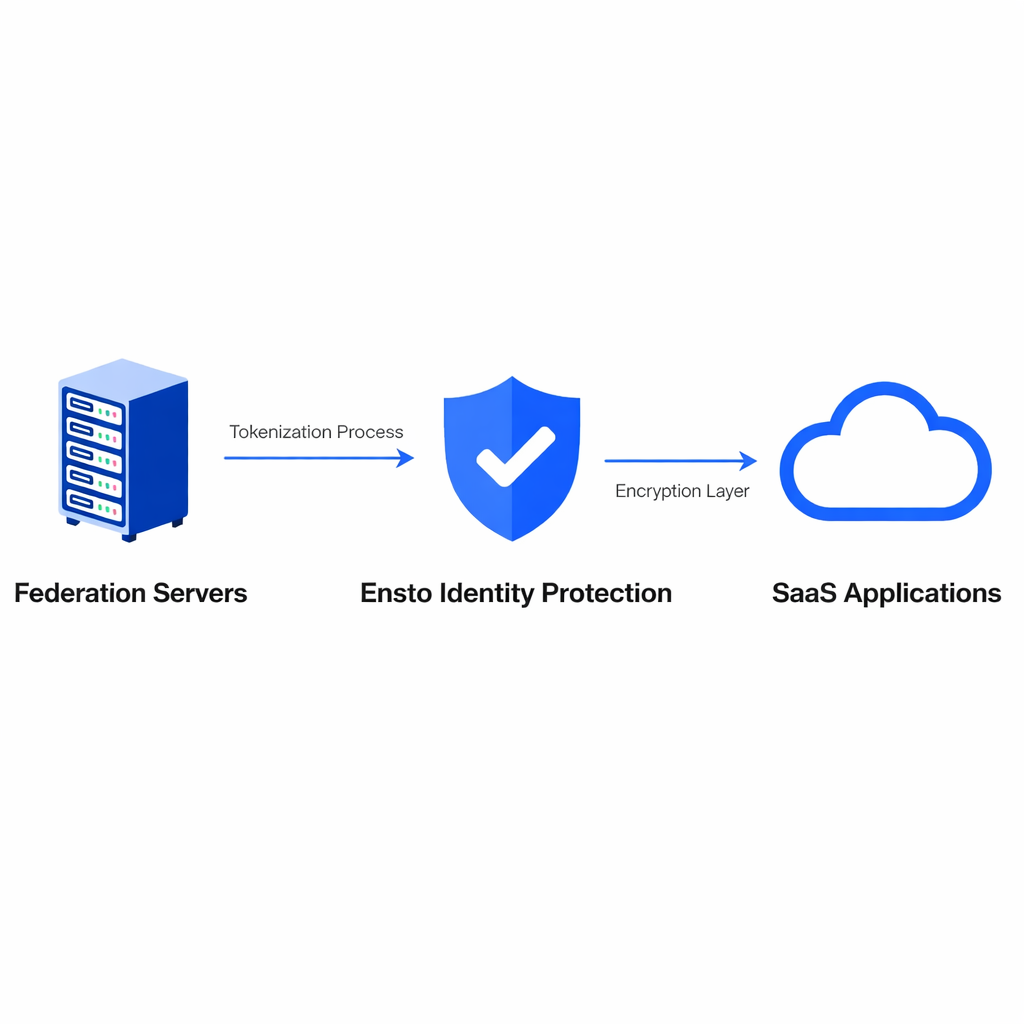
How Ensto Complements Your Federated IAM Architecture to Secure Multi-Domain Identities Executive Summary for CISOs The modern enterprise has become a constellation of identity sources. Your workforce identities originate from corporate directories, while vendors bring their own credentials, partners integrate via federated systems, and clients access your applications through their own identity providers. This distributed identity ecosystem—spanning AWS, Azure, Ping, Okta, Microsoft Entra ID, and countless SaaS applications—creates profound security and compliance challenges. The core problem isn’t your IAM platform. It’s what happens to identity data after authentication. Your federation server (whether AWS IAM Identity Center, Ping Identity, or Azure Entra ID) excels at one thing: authentication and authorisation. It verifies “who you are” and “what you can access.” But it was never designed to protect the actual identity data itself once it enters your SaaS applications, data stores, and network infrastructure. That’s where Ensto enters the architecture. Ensto is not a replacement for your IAM. Instead, it’s a complementary data protection layer that works downstream of your federation infrastructure. By fragmenting, encrypting, and distributing identity data across 25,000+ encrypted storage combinations, Ensto eliminates the single largest vulnerability in federated environments: identity data duplication and exposure. Part 1: Understanding Federation and the Identity Data Problem What Is Federated Identity Management? Federated identity management enables organisations to establish trust relationships with external identity providers so users authenticated in one system can access resources in another without managing separate credentials. Instead of storing credentials locally, you trust an external Identity Provider (IdP) to verify “who the user is,” and the application (Service Provider) grants access based on that trust. The primary protocols enabling federation are SAML 2.0 (used in enterprise for 20+ years), OpenID Connect (modern, OAuth-based), and OAuth 2.0 (authorisation framework). When a user attempts to access a federated resource: The application redirects to your federation server Your federation server may redirect to an external IdP (if it’s a partner or vendor) The IdP authenticates the user The IdP returns identity attributes in a signed assertion or token Your federation server creates a session The user accesses the application Here’s the critical issue: Once the application receives identity attributes (name, email, department, phone), it stores this data in its database. That identity data is now duplicated in: The application’s user database Application audit logs Your SIEM system’s ingested logs Backup systems Third-party analytics tools connected to the app Potentially dozens of other systems The Duplication Problem at Scale Research shows 60% of enterprises experience identity data duplication across SaaS applications. Consider a mid-size enterprise: 500 internal employees (federated via Azure Entra ID) 200 active vendors (federated via various IdPs) 300+ partner users (federated through partner organisations) 15 primary SaaS applications (CRM, HR, Finance, Collaboration, etc.) Each application stores identity data: name, email, department, phone, manager, and custom attributes. If 1,050 total users are active across 15 applications, that’s 15,750 identity records scattered across your infrastructure. In a breach, this multiplied exposure is catastrophic. Compliance Impact: GDPR requires data minimisation. Storing the same identity in 15 locations is indefensible. CCPA gives users the right to deletion—if identity is duplicated across 15 systems, you must delete from all 15. Gaps create violations. Breach Impact: In a SaaS compromise, attackers find 15,750 records instead of 1,050. Notification costs multiply by 15x. Regulatory fines escalate. Customer trust erodes exponentially. Part 2: How Federation Systems Work Today Architecture Pattern: Hub-and-Spoke Model Most enterprises use hub-and-spoke architecture, where a central IdP connects to multiple applications. AWS IAM Identity Center acts as a hub connecting to AWS accounts, Salesforce, ServiceNow, and partner systems. Ping Identity serves as a hub for organizations with complex attribute mapping and policy requirements. Azure Entra ID acts as both a hub (for the internal workforce) and connects to B2B partners. In this architecture, federation servers handle authentication, authorisation policy, and attribute enrichment. When a user authenticates through federation, the server returns signed SAML assertions or OIDC tokens containing identity attributes. Applications receive these attributes and persist them to databases. Example Flow: A vendor from a partner organisation needs Salesforce access. They authenticate through their company’s Okta instance, which trusts your federation server via SAML. Your federation server creates a session, and Salesforce receives a SAML assertion with the vendor’s name, email, department, and custom attributes. Salesforce stores this data in its user database, logs, and audit systems. Now this vendor’s identity exists in your federation server, Salesforce’s database, Salesforce’s logs, your SIEM, and potentially dozens of other systems. The vulnerability: Federation protocols (SAML, OIDC, OAuth) were designed for authentication and authorization—not for protecting identity data after authentication. They solve “how do we trust each other?” not “how do we protect the data we’re trusting?” Part 3: Ensto’s Role as a Data Protection Layer What Ensto Actually Is (And Isn’t) Ensto is NOT: A replacement for your IAM/federation system An authorisation engine Ensto IS: A data protection layer for identity information A PII tokenisation platform A cryptographic identity security system An application-centric identity governance tool An enterprise communication tool Ensto operates downstream of your federation. After your IdP authenticates a user and issues a session token, Ensto transforms identity data through three steps: Fragmentation: Identity attributes are split into meaningless fragments (name split and separated from email, separated from phone, separated from department) Encryption: Each fragment is encrypted using best-in-class encryption Distribution: Encrypted fragments are dispersed across 25,000+ databases and fragmentation combinations The result: Applications receive identity tokens instead of actual PII. These tokens are non-exploitable—if stolen, they’re meaningless without the fragmentation key stored in Ensto’s infrastructure. Integration Architecture: AWS IAM Identity Center + Ensto Your AWS environment uses IAM Identity Center as the federation hub. Corporate directory feeds into it, and it connects to AWS accounts and federated SaaS applications. Without Ensto: Identity attributes flow from IAM Identity Center to applications, which store them directly in databases. When Salesforce, ServiceNow, or Slack authenticate users, they receive tokens. Applications store tokens, not identity data. If any application is breached, attackers find only cryptographically
The boardroom falls silent. Another breach headline. Another apology email drafted. Another lawsuit was filed. And somewhere in that noise, your organisation is watching customers—loyal customers—quietly slip away to competitors who promise something your team can no longer deliver: absolute confidence that their data is secure. For CIOs and CISOs, this isn’t just a security problem. It’s an existential business threat disguised as a technical challenge. The truth that enterprises are wrestling with today is uncomfortable: traditional security is no longer enough. Encryption locks doors. Firewalls build walls. But attackers have learned to pick both. What enterprises desperately need—what your customers are demanding—is a fundamental shift in how identity data is protected. Not just encrypted. Not just monitored. But rendered completely unintelligible to anyone without authorisation, even those who’ve compromised your systems entirely. This is where Ensto enters the conversation. Powered by Keywix‘s patent-pending IdentityAI technology, Ensto transforms identity data into something that cyberattacks simply cannot exploit. It’s not about adding another layer to your security stack. It’s about eliminating the single greatest vulnerability in your enterprise ecosystem: the duplication of customer identity data across your SaaS applications. Let’s talk about what’s really at stake. The Hidden Vulnerability That Attackers Are Exploiting Here’s a statistic that should make every CIO lose sleep: 95% of enterprise cyberattacks involve duplicated identity data stored across multiple SaaS applications. This isn’t a theoretical risk. This is your operational reality today. Your CRM has customer names and emails. Your HR system has them again. Your communication platform has them a third time. Your financial application has them a fourth time. Every duplication is another attack surface. Every copy is another opportunity for exfiltration. Sixty per cent of the Fortune 1000 companies reported user data loss in the last decade. That’s not a future concern—that’s what already happened. The mathematical problem is merciless: Cyberattacks target duplicated identity data. When attackers breach your perimeter—and let’s be honest, they will—they don’t need to hunt for treasure. The treasure is everywhere, duplicated across your entire application ecosystem. And here’s where the business impact becomes undeniable: enterprises now incur $4 million+ on average per data breach. But the financial cost is only half the story. When Trust Dies, Growth Dies With It: The Hidden Cost of Identity Anxiety Imagine your enterprise landing a major prospect. Detailed discovery complete. Technical evaluation finished. Budget approved. Everything is ready to go. Then comes the security review. Your prospect’s CISO asks the hard questions: “Where is our data stored? Can you guarantee it won’t be duplicated across your systems? If you’re breached, what’s the worst-case scenario?” And if your answer reveals that customer identity data is scattered across multiple applications, stored in encrypted but still-recognisable form across 5+ different databases, your prospect doesn’t say “yes”—they disappear. This happens thousands of times across enterprises every quarter. And it’s quantifiable. 58% of prospects opt out of mailing lists, citing data concerns. 60% reject data-for-download exchanges. 75% avoid signups because of data privacy concerns. 80% abandon demo forms over data privacy anxiety. These aren’t small friction points. These are massive revenue leaks disguised as “low conversion rates” in your sales pipeline. For an enterprise SaaS company processing just 100 demo requests per month, if 80 of those prospects abandon due to data anxiety, that’s 80 qualified opportunities going to a competitor. Over a year, that’s 960 lost opportunities. At an average deal size of $100,000, that’s $96 million in annual lost revenue from security anxiety alone. But here’s what most security teams don’t realise: this isn’t inevitable. This is a choice. The Trust Multiplier Effect: What Happens When You Eliminate Identity Anxiety Organisations that solve the identity data problem don’t just reduce risk. They unlock a cascading effect across their entire business: Wider Enterprise Adoption When prospects conduct their security evaluations and discover that your organisation has implemented a “zero data duplication” model—where identity data exists as fragmented, encrypted, and completely unintelligible tokens rather than recognisable records—their confidence skyrockets. They ask: “If they get breached, what exactly do attackers get? Unintelligible fragments?” The answer is yes. This single architectural difference removes the greatest barrier to adoption. Organisations addressing identity anxiety see 3.2x higher deal conversion rates. That’s not incremental improvement. That’s transformational. More Demos Completed Remember those 80 prospects abandoning demo forms? When you can confidently state that your platform uses unintelligible data architecture—that even if a breach occurs, the attacker gains nothing of value—demo form abandonment drops dramatically. Companies implementing robust data protection measures see demo-to-trial conversion rates improve substantially compared to organisations without transparent security practices. Prospects aren’t just willing to attend demos. They’re eager to see how your security works. Organisations with strong customer trust see referral rates 5-6x higher than the industry average. The Ensto Difference: Turning Data Into an Unhackable Asset Traditional identity management platforms work like this: User data is encrypted at rest and in transit It’s stored centrally (or in duplicated form across apps) Access is controlled through IAM policies If breached, attackers get real data at best or encrypted data at worst — which they can potentially decrypt or exploit over time The Ensto approach is fundamentally different: The Four-Pillar Architecture Fragmentation Beyond Recognition Ensto breaks identity data into meaningless fragments. Your customer “John Smith, john@company.com , SSN 123-45-6789″ doesn’t exist anywhere as a recognisable record. It exists as distributed fragments: “jk@”, “45678”, “mith”, “Smith”, etc. No single fragment reveals identity. No combination of fragments yields usable data without the Ensto system reconstructing them. Military-Grade Encryption Each fragment is encrypted using best-in-class cryptography. The encryption doesn’t just protect data at rest—it creates an additional security layer that even unintelligible data cannot traverse. Distributed Across 25,000+ Database Combinations Fragments aren’t stored in one database. They’re intelligently dispersed across 25,000+ possible database and collection combinations. An attacker would need to compromise multiple systems simultaneously, navigate through a distributed infrastructure, and still face encrypted, unintelligible fragments. The attack surface complexity becomes mathematically impractical. Instant Unification Through Patent-Pending Technology Despite being
You’ve built a fantastic SaaS application. Your CRM works perfectly. Your HR software processes thousands of employee records. Your financial platform handles millions in transactions. Your workflow system keeps teams aligned across continents. But here’s the problem nobody talks about: each of these applications is storing the same customer and employee data independently. Sophie’s profile lives in your CRM. Her emergency contact information is duplicated in your HR system. Her phone number is stored in your communications platform. Her email address exists in your financial app. Her profile picture is saved separately in your workflow management tool. This isn’t just messy. It’s dangerous. It’s expensive. And it’s keeping you from focusing on what you actually want to build. The Hidden Cost of Data Duplication Most growing companies don’t realise how much liability they’re carrying until it’s too late. When you store the same customer or employee information across multiple systems, you’ve essentially created multiple targets for attackers. A data breach doesn’t just mean losing data once; it means losing it ten times over if that person’s information exists in ten different applications. The numbers are sobering. The average cost of a data breach in 2025 has reached $4.88 million per incident—a 10% increase from the previous year. And if your company stores customer data across multiple systems and environments, the costs climb even higher. Breaches involving data spread across multiple environments average $5.05 million, compared to those kept primarily on-premises at $4.01 million. “Beyond the financial hit, there’s the customer trust factor. When you experience a data breach, you have to notify customers. You have to explain that their information was exposed. You have to implement credit monitoring. You have to restore damaged relationships.” 58% of customers opt out of mailing lists after a breach. 60% reject any future data-for-download exchanges. 75% avoid signing up for new services from companies that have had privacy incidents. 80% abandon demo forms citing data privacy concerns. One breach doesn’t just cost millions in immediate response. It costs you customer lifetime value, market reputation, and future growth potential. The Compliance Nightmare That Never Ends If data duplication were just a security issue, that would be bad enough. But modern privacy regulations make it exponentially worse. GDPR, Australia’s Privacy Act, and countless other regulations all require the same thing: you must know where customer data lives, who has access to it, and how you’re protecting it. Auditors want to see your data inventory. Regulators want proof that you’re minimising data collection to only what’s necessary. Customers want to know they can request deletion and have it actually happen. When Sophie’s information exists in five different databases, fulfilling a data deletion request becomes a nightmare. Did you delete it from the CRM? What about the HR system? The communications app? The financial records? The workflow tool? If you miss one, you’re not compliant. You’re in violation. Compliance officers lose sleep over this. “We have a data privacy incident,” they tell their CEO, “because we discovered customer information in a system we forgot we had.“ Australia’s recent Privacy Act reforms, effective June 2025, have raised the bar significantly. Businesses now face stricter data security standards, faster breach notification requirements, and the introduction of a statutory tort for serious privacy invasions. The Australian Information Commissioner has been given stronger enforcement powers, meaning penalties for non-compliance are now more severe than ever. For SaaS companies operating across borders, this is a compliance minefield. Different rules in different countries. Different definitions of what constitutes personal information. Different requirements for how long you can retain data. Why Your Development Team Is Frustrated Here’s something that rarely gets discussed at board meetings: your engineers are frustrated. Every time your company adds a new SaaS tool—a new communications platform, a new analytics engine, a new financial system—your development team has to figure out how to integrate it with existing systems. They have to map data fields. They have to build connectors. They have to maintain those connectors as software versions change. If you have 10 SaaS applications, you’re not just running 10 systems. You’re running potentially 45 different integrations (that’s the number of possible connections between 10 systems). And each integration is a potential point of failure. Each integration requires ongoing maintenance. More importantly, each integration means more places where customer data has to be copied, transformed, and transmitted. Each copy is another security risk. Each transformation is another place where data quality can degrade. Your CRM team wants to focus on building better customer segmentation and predictive analytics. They shouldn’t be spending development cycles managing data synchronization with the HR system. Your HR team wants to build better employee experience tools. They shouldn’t be spending engineering resources making sure employee records sync correctly with the communications platform. This is where your competitive advantage gets lost—not in the product features you fail to build, but in the infrastructure work that consumes your engineering resources. The Ensto Approach: Applications Over Information What if your applications didn’t have to store customer data at all? What if your CRM focused entirely on managing customer relationships and closing deals—without worrying about where customer profile information actually lives? What if your HR system could handle employee workflows, performance reviews, and compensation management—without maintaining duplicate copies of employee contact information? What if your financial application could process transactions and generate reports—without storing personally identifiable information (PII)? This is the concept behind Ensto’s “Applications Over Information” philosophy. Instead of each application independently storing customer and employee data, Ensto IdentityAI acts as a dedicated identity platform that secures, manages, and controls all identity-related information. Your applications tell Ensto what to do with customer information—authenticate, update, or communicate—without ever touching or storing the data themselves. How It Works in Practice Imagine Sophie is a customer. She creates a profile in your system. Her information—name, email, phone number, address, payment method, preferences—goes into Ensto. Your applications don’t store Sophie’s information. They store references to Sophie and the specific data they need to
Remember when having ONE email address for everything was considered normal? Yeah, those days are over. We live in a world where you’re literally different people depending on who you’re talking to. Your boss doesn’t need to know about your gaming tournaments. Your gaming squad doesn’t need your LinkedIn. Your family group chat definitely doesn’t need your shopping wishlist. Yet somehow, the old digital card industry expects you to smoosh all of that into one static, boring, data-stealing profile that costs you money every single month. It’s giving outdated energy. It’s giving corporate greed. It’s giving 2010. Gen Z user are displaying their professional work profile on #Connecto Welcome to Connecto—where your digital identity actually makes sense. The Problem Nobody Wanted to Talk About Let’s be real for a second. That digital card everyone told you to get? It’s basically a digital fossil. You know the one—you pay for it monthly (because apparently existing online costs money now), and it shows the exact same boring information to literally everyone. Your boss sees the same thing as the barista at your favourite coffee shop. Your college friends see the same thing as your great-aunt Karen. It’s the definition of a one-size-fits-all solution, and we all know how those turn out. But here’s where it gets actually concerning. These static digital cards? They’re data vacuum cleaners. Every time you update your profile, every single interaction, every click—someone’s collecting it. You’re basically paying money to let companies harvest your information. And they’re not using it to make your life better. They’re using it to target you, profile you, and sell access to that data to whoever’s willing to pay. It’s invasive, it’s uncomfortable, and frankly, it should be illegal. But it’s not, so here we are. The worst part? You thought you had to accept this. You thought this was just how digital networking worked in 2025. Limited options, monthly fees, constant data leakage, and a profile that makes you look like a robot who works in accounting (no offence to actual accountants—we see you). Enter Connecto: The Plot Twist Nobody Saw Coming Then Connecto showed up like that friend who actually gets it. The one who understands that your identity isn’t a flat, two-dimensional thing. It’s layered. It’s nuanced. It’s actually about five different versions of you depending on the context, and that’s not weird—that’s just being a functional human in 2025. Connecto isn’t asking you to be one person. It’s celebrating the fact that you’re like six different people, and that’s actually really cool. The core idea is simple but revolutionary: create different profiles for different parts of your life. Not because you’re fake or two-faced, but because you’re complex and interesting. Revolutionary, right? Your Work Profile: Professional Without Being Boring Let’s start with your work profile. This is the you that shows up to the office, online class, internship, or wherever you’re earning your coins. This version of you is motivated, professional, and ready to collaborate. You probably have some achievements you’re actually proud of. Maybe you’ve completed some projects that don’t suck. Your work profile is the place to showcase exactly that—without your gaming stats, without your shopping addiction, without your family photos. When someone from work asks for your contact info or your digital profile, you send them your Connecto work profile. They see what they need to see. They don’t see that you spent last weekend trying to get a platinum medal in your favourite game. They see your professional skills, your availability, and your real value to a team. It’s boundaries, but make it digital. And here’s the thing that makes it actually powerful: you stay in control. You decide what goes in this profile. You decide what information is shared, when it’s shared, and with whom. This isn’t some algorithm deciding what makes you look employable. This is you, being intentional about your professional brand. Your Friends Profile: The Real, Messy, Authentic You Now your ‘FRIENDS’ profile? This is where you get to be real. This is where your inside jokes live. This is where you share your actual personality—the one that thinks terrible memes are hilarious, the one that has strong opinions about everything, the one that your boss doesn’t need to meet. Your ‘FRIENDS’ profile is saturated with personality. Your favourite music, your hot takes, your sense of humour, the things you actually care about. If your work profile is a business card, your friend’s profile is like hanging out with you. It feels like the real you because it is. And when you’re at a party and someone’s like “yo, what’s your Connecto?” you can just send them your ‘FRIENDS’ profile without worrying they’re going to see something they’re not supposed to see. You’re not overthinking every detail because it’s already compartmentalised. It’s liberating, honestly. Your Family Profile: Keeping the People You Love in the Loop Family is complicated. You might be living your best independent life in the city, but your parents still want to know you’re eating vegetables and not doing anything dangerous. Your grandparents want to feel connected to you. Your cousins actually think you’re cool, even if you can’t see it. Your family profile lets you share what matters to your people without making it weird. You can update your location so your parents know you made it to campus safely. You can share your achievements without it feeling like bragging because it’s a family-only space. You can be vulnerable in a way you can’t be on your work profile or even with friends. Your family profile is for the people who actually care if you’re okay. This is where privacy actually matters. Your family information shouldn’t be visible to your boss, to random people at networking events, or to potential dates scrolling through your profile. Connecto makes sure of it. Your Shopping Profile: Curating Your Style Let’s talk about something Gen Z and Gen Alpha actually care about: shopping. Your shopping profile is your digital
Identity management is no longer just an IT necessity—it is the single most powerful lever for building and sustaining customer trust. In the era of relentless cyberattacks, evolving privacy regulations, and increasingly digital consumer expectations, business leaders in marketing and client relations must prioritise identity management at the board level, positioning it as the cornerstone of brand reputation, loyalty, and growth. The Trust Crisis: Why Identity Management Demands Executive Attention Businesses today face an existential challenge: digital trust has become the currency of customer loyalty, but its foundations are under siege. In the past year, 67% of organisations faced increasing cyberattacks, with 43% losing customers and 47% struggling to attract new ones after a breach—double the numbers seen in 2023. Privacy fears directly influence consumer behaviour: over 80% of global consumers have abandoned brands due to data privacy concerns in the last 12 months. In Australia, 71% of consumers have opted out of purchases due to lack of trust in data handling, and 70% of online shoppers cite privacy as their top reason for abandoning purchases. Even a single breach can cause customer churn rates to spike by 2.67% to 7%, costing millions, while negative publicity lingers far longer than technical recovery and can irreparably damage brand reputation. Today, consumer expectations around data transparency and control are uncompromising—if privacy feels intrusive or unclear, 67% will avoid your website outright and 57% will skip your app entirely. The Ensto Difference: Reimagining Identity Security for Brand Trust Ensto – The IdentityAI platform turns the problem of identity data liability into an opportunity for customer trust. Unlike traditional systems, Ensto uses its patent-pending data fragmentation, encryption, and distributed storage—breaking personal information into meaningless fragments, dispersing it across 25,000+ databases, and securing it with best-in-class cryptography. Even in the event of a breach, attackers find nothing of value—unintelligible data tokens replace readable customer information, and enterprises can instantly restore secure identities with minimal business disruption. This approach elevates privacy without replacing existing IAMs. Instead, it: Cuts breach impact by up to 70% Unifies customer identity across SaaS apps without duplicating sensitive dataBoosts user confidence, improves sign-up rates, and supports regulatory compliance (GDPR, PA88, etc.) Reduces onboarding costs and friction for both clients and developers Ensto’s model is not just about keeping IT systems safe—it’s about safeguarding business growth and customer relationships in a world where trust is fragile and every interaction matters. Why CMOs and Chief Client Officers Must Lead Identity Transformation Dividing responsibility for identity between IT, HR, and security is no longer tenable. Modern privacy laws and consumer expectations position marketers and client leaders as the frontline stewards of brand trust. For CMOs: Privacy as Brand Value and Growth Engine “Privacy must now be a brand value, not a checkbox. Trust drives growth—permission and transparency win.” Transparency, Consent, and Control Consumers want to know how their data is used—and to opt-in. CMOs must guide their teams to collect only what’s necessary, be explicit about consent, and make privacy policies clear and accessible. Storytelling for Trust Every marketing touchpoint is an opportunity to reinforce the brand’s respect for customer data. Transparent collection practices and privacy-first messaging enhance loyalty and brand equity. Privacy as KPI Modern marketers build metrics around first-party data use, consent rates, and transparency, embedding privacy into customer experience and campaign effectiveness. For Chief Client Officers: Customer Experience Anchored in Identity Security “The CCO is the voice of the customer to the C-suite and must champion customer-centric, trust-building strategies across every journey.” Seamless, Secure Experiences Customers demand frictionless transactions and robust protection. CCOs must champion that secure identity verification is integral to onboarding, renewals, and service. Proactive Communication Talking openly about security practices relieves customer anxiety. CCOs should make privacy measures part of the ongoing client conversation, not just a post-breach scramble. Retention and Advocacy Trust breeds loyalty. By deeply understanding and addressing security and privacy concerns, CCOs can drive higher retention, positive word-of-mouth, and increased revenue from existing customers. Summary: Why Identity Must Be a Board-Level Priority Identity management is the new foundation of digital trust, brand reputation, and sustainable growth. IT leaders alone can’t own this imperative—chief marketing officers and chief client officers must treat it as central to customer experience and business strategy. Businesses that get identity right earn loyalty, build resilience, and seize competitive advantage. Privacy by design, transparency, and user control are the keys to surviving and thriving in an age of cyber risk and customer scepticism. The boardroom conversation must shift: secure identity isn’t just about compliance—it’s about building the lasting trust that powers every relationship and every dollar of growth.