Every organisation today manages thousands—sometimes millions—of user identities. But here’s a question: how many of them are duplicated across various systems? It’s a scary thought, right? You’d expect every employee, customer, or vendor to have one verified record, but in reality, that’s rarely the case. Between HR systems, CRMs, SaaS apps, and legacy databases, the same person can exist in multiple places under slightly different records. That’s what experts call identity duplication — and it’s quietly amplifying security risks everywhere. This post will unpack what identity duplication really means, how it fuels modern breaches, and what forward-thinking platforms like Keywix are doing to fix it for good. What Exactly Is Identity Duplication? Let’s start simple. Identity duplication happens when multiple records represent the same individual across different systems or apps. Picture this: An employee has one account in your HR software, another in your payment system, and yet another in your project tool—all under slightly different usernames, email addresses, phone numbers, or nicknames. A customer’s data lives in your billing platform, your marketing CRM, and your helpdesk—each version slightly out of sync. This duplication happens naturally in today’s cloud-first, remote-work world. Every new tool you add to your tech stack is another potential identity silo. Before you know it, your organisation’s “identity landscape” looks more like a digital jigsaw puzzle—full of overlapping, disconnected pieces. How Duplication Multiplies Risk Here’s the uncomfortable truth: each duplicate identity is another open door for attackers. When your systems can’t/don’t talk to each other, security blind spots form. Duplicates cause: Weak or inconsistent authentication — some systems may enforce MFA, others might not. Forgotten or inactive accounts — perfect for attackers to exploit. Gaps in visibility — IT teams can’t see who really has access to what. A 2024 cybersecurity study found that over 40% of breached credentials belonged to unused or duplicated accounts. That means hackers aren’t always breaking into your main systems—they’re waltzing in through the forgotten side doors your own data created. So, while identity duplication might sound like a data-entry problem, it’s really a threat multiplier. The Hidden Costs for Businesses Security risks are just the start. Identity duplication drains money, time, and trust in subtle yet significant ways. Operational waste: Paying for extra software licenses for the same person. Compliance chaos: Under laws such as GDPR, the Australian Privacy Act, or India’s DPDP, proving data accuracy becomes almost impossible when duplicates exist. Customer frustration: Conflicting profiles lead to botched support, mismatched preferences, and broken experiences. Audit headaches: The more identities you have to track, the more complex (and costly) your security reviews become. It’s like having a thousand ghost employees haunting your databases—each one adding clutter and confusion. Why Traditional IAM Tools Struggle Traditional Identity and Access Management (IAM) systems were never designed to solve duplication—they were built to handle authentication. Most IAM tools still rely on static directories and manual syncs between disconnected platforms. In hybrid, SaaS-heavy environments, that’s like trying to herd cats with a clipboard. The result? Identity sprawl. Your data exists everywhere, but ownership and control exist nowhere. That’s why newer approaches—using AI-based identity graphing and automation—are essential. They map and unify identities dynamically, spotting duplicates before they become security holes. How Identity Duplication Fuels Modern Breaches Imagine this: A company has an old admin account belonging to an employee who left last year. HR deactivated their main profile—but forgot about the duplicate in the cloud app. Months later, a hacker finds those old credentials in a dark web dump and logs in unnoticed. From there, it’s game over. Attackers move laterally between systems using duplicate credentials, bypassing security alerts because the “real” account still looks fine. This is why identity duplication is so dangerous—it hides attacks in plain sight. The breach doesn’t just happen; it multiplies quietly across every copy of your user data. Privacy and Compliance Implications Beyond breaches, identity duplication is a privacy nightmare. “Right to Be Forgotten” requests? Almost impossible to fulfil when you have the same user scattered across five databases. Data minimisation? Gone. Transparent data handling? Out the window. Duplicated identities expose PII (Personally Identifiable Information) across multiple systems, thereby increasing the likelihood of leaks and compliance violations. This is where privacy-first identity models come in—they’re designed to give users control while reducing organisational data exposure. Preventing Identity Duplication Okay, so how do you stop this silent chaos? Here’s a roadmap any organisation can start with: a. Centralized Identity Architecture Unify your identity data under a single, secure identityAI vault. Instead of duplicating user data, systems connect to one verified source. b. Periodic Identity Audits Regularly scan your databases for duplicate or inactive profiles. Merge or remove what’s unnecessary. c. Adopt Modern Identity Management Solutions Utilise platforms like Keywix’s ENSTO, designed to secure user identities without ever copying data across systems. These platforms bring the principle of identity singularity to life—one verified identity that connects everywhere securely. d. Automation & AI Let AI do the heavy lifting. Machine learning can detect anomalies, redundant records, and inconsistent identity data in real time. Keywix’s Perspective: IdentityAI as the Cure At Keywix, we believe the best way to stop identity duplication is to eliminate the need for identity-data duplication Our privacy-first, user-controlled identity management model empowers users to own their digital identity in the org vault. Instead of creating multiple copies of the same data across services, Keywix connects systems through verified tokens, ensuring one unified identity—no replication, no exposure. Our product Connecto extends that same philosophy into communication. It’s not just a secure communications app—it’s a privacy-first identity platform: No tracking or data harvesting. AI-powered spam and identity protection. Smart digital contact cards that let users share securely—no app required on the other side. It’s communication redefined for a privacy-conscious world. In short: Keywix advocates for identity singularity—one digital self, verified, secure, and truly yours. The Future: From Duplication to Unification We’re entering an era where passwordless authentication, decentralised credentials, and AI-driven
Cyberattacks aren’t just scary news stories—they’re real threats for every business today. A single stolen credential or weak security measure can put your employees, clients, and sensitive data at risk. This is where ENSTO comes in. More than just a login tool, ENSTO is a next-generation identity solution designed to go beyond authentication. It focuses on business identity protection, keeping your company safe while letting your team work efficiently. Think of it as a security expert that never sleeps, watching over your digital assets 24/7. If you’ve ever wondered, “Are the business access controls enough?” or “How can I protect my customers’ data in the event of an attack?”—this article is for you. Why Traditional IAM aren’t Enough For years, passwords, OTPs (one-time passwords), along with multi-factor authentication (MFA), were considered secure. But today’s hackers are smarter and faster. Phishing attacks trick employees into revealing credentials. Credential stuffing uses leaked passwords from one site to access multiple accounts. Insider threats involve employees or contractors with access misusing data—sometimes accidentally, sometimes intentionally. Even MFA can fail if it’s predictable or not adaptive. The consequences? They’re serious. Weak identity protection can lead to: Data breaches, leaking customers’ and employees’ information. Financial loss from ransom demands holding customers’ identity for ransom Damage to your company’s reputation and loss of client trust. Imagine building a loyal customer base for years, only to see trust evaporate overnight due to a cyberattack. That’s why modern businesses need solutions that go beyond basic authentication. How ENSTO Protects Business Identity ENSTO takes a holistic approach to business identity protection. It doesn’t just secure logins—it protects identities across your entire digital ecosystem. Here’s how it works: Adaptive Authentication & Behavior Analysis ENSTO monitors how users interact with your systems. If it notices something unusual—like seeking multiple users’ information—it flags it immediately. This means suspicious activity is stopped before it becomes a breach. Secure Identity Lifecycle Management From onboarding a new employee to deactivating an account after they leave, ENSTO ensures every identity is managed properly. No more forgotten accounts creating security loopholes. Real-Time Threat Detection & Alerts ENSTO sends instant alerts whenever it detects a threat. You don’t have to wait for a breach to appear—it gives you the power to act immediately. Seamless Integration with Existing Systems ENSTO works alongside your current apps, cloud platforms, and SaaS tools without disrupting workflows. Security shouldn’t slow your team down—and ENSTO gets that. In short, ENSTO treats your company’s identity as a high-value asset—because once it’s compromised, every other system is at risk. Boosting Cyber Resilience with ENSTO So, what is cyber resilience? Simply put, it’s your business’s ability to survive and adapt during a cyberattack. Think of it as a digital immune system: detecting threats, containing damage, and keeping operations running. ENSTO strengthens cyber resilience in multiple ways: Preventing Lateral Attacks & Identity Duplication: Hackers often move sideways through systems after gaining access. ENSTO stops this by tightly controlling identities. Reducing Attack Surfaces Across SaaS & Cloud Platforms: Every connected app can be an entry point. ENSTO secures these connections so attackers have fewer opportunities. Rapid Response & Recovery: If a breach occurs, ENSTO helps your team respond immediately, minimising downtime and data loss. Example scenario: A hacker tries to log into your CRM using stolen credentials to steal users’ personal information. ENSTO tokenises all users’ PII, allowing your CRM to function without keeping customer PII and use ENSTO for PII-related applications. Thanks to ENSTO, the hacker never gained customer personal information from the CRM. Business Benefits of ENSTO Beyond security, ENSTO delivers practical benefits for your business: Operational Efficiency: Employees can log in securely without constant interruptions or extra steps. Security doesn’t slow productivity. Regulatory Compliance: ENSTO helps meet GDPR, CCPA, and other regulations. No more worrying about fines for failing to protect sensitive data. Trust & Reputation: Clients and partners see that you prioritise business identity protection. Trust grows, and your brand strengthens. In other words, ENSTO not only protects your business but also helps it thrive. The Future of Identity Protection The cybersecurity landscape is evolving fast. Trends like Zero Trust, passwordless authentication, and AI-driven security are no longer futuristic—they’re essential. ENSTO aligns perfectly with these trends, offering a forward-thinking approach that keeps your business ahead of threats. Imagine a workplace where PII is invisible, threats are detected automatically, and cyber resilience isn’t just a goal—it’s a reality. Conclusion Traditional authentication isn’t enough anymore. ENSTO goes beyond passwords, providing complete business identity protection and enhancing your cyber resilience. Don’t wait for a breach to rethink your security. With ENSTO, you protect your employees, customers, and reputation while keeping operations smooth and compliant. Because in today’s digital world, identity isn’t just a login—it’s the backbone of your business. Secure it wisely with ENSTO.
The SaaS Security Paradox Cloud-based tools are the heartbeat of modern business. CRMs, HR platforms, collaboration apps — you name it, enterprises and startups rely on them to scale faster and operate smarter. But with that agility comes a hidden risk — your sensitive customer data is now scattered across dozens of SaaS platforms. Every tool you adopt adds convenience, but it also multiplies exposure points for cyber threats. Traditional security systems, like IAMs (Identity and Access Management platforms), focus on who gets in — not what happens once they’re in. They authenticate users, manage access, and enforce login policies. But inside those SaaS apps? Your actual data remains vulnerable. That’s the SaaS security paradox — you’re locking the doors while the valuables inside are left unguarded. And that’s exactly where ENSTO changes the game. Meet ENSTO — The Next-Generation Identity Management Platform Built by Keywix, ENSTO is a modern solution for managing identity in a secure, privacy-first way. It’s built to help individuals and businesses connect with trust. As a Next-Generation Identity Management Platform, ENSTO enables secure interactions across systems without ever compromising your data. Whether you’re a fast-growing startup or an enterprise modernising its identity infrastructure, ENSTO offers an affordable, AI-ready, and futuristic way to manage identities safely. It’s designed not just to protect access, but to protect information. Because let’s face it — security isn’t just about keeping people out; it’s about making sure your data stays unreadable, unexploitable, and unintelligible to anyone who shouldn’t have it. The Limitations of Traditional IAMs IAMs do a great job at authentication, authorisation, and access management. They’re your digital gatekeepers. But that’s also where they stop. Once a user gains access to a SaaS platform, the IAM’s job is done. It doesn’t control what happens next — how data is duplicated, stored, or shared. Here’s where the cracks start to show: Data duplication chaos: Customer or employee information often exists across multiple SaaS systems. Each copy becomes another potential breach point. Weak PII protection: IAMs encrypt passwords, but they don’t always protect the personally identifiable information (PII) inside your SaaS apps. Insider risk: Even legitimate users can mishandle or expose sensitive data unintentionally. So while IAMs keep intruders out, they can’t guarantee what happens to your data once they breach the walls. Enterprises today need something stronger — a layer that goes beyond encryption, turning your sensitive data into unintelligible information that’s useless to attackers. ENSTO: Built for the Privacy-First Enterprise ENSTO was designed precisely for this modern challenge. Rather than replacing your IAM, ENSTO complements it — adding a layer of deep, privacy-first protection to your existing identity framework. Its core innovation, ‘Unintelligible Data At Rest’ technology, ensures that even if a data breach occurs, the stolen information is indecipherable. It goes beyond standard encryption by transforming data into a form that simply cannot be reversed or exploited. Think of ENSTO as a shield that works silently in the background, ensuring your sensitive data remains safe — always. ENSTO doesn’t replace your IAM — it empowers it. Key Advantages of ENSTO for SaaS Data Protection a. Data Duplication Control SaaS sprawl often means multiple apps holding the same identity information. ENSTO solves this problem by controlling and reducing unnecessary duplication. With fewer data copies floating around, your attack surface shrinks — and your compliance posture improves. b. SaaS PII Protection & Tokenisation ENSTO secures personally identifiable information using tokenisation and unintelligible data transformation. Even if a hacker breaches your system, they’ll find nothing but scrambled data that’s impossible to reconstruct. c. Cyber Resilience Cyberattacks are inevitable, but data loss doesn’t have to be. ENSTO builds resilience into your SaaS ecosystem, ensuring data integrity and continuity even when a system is compromised. d. Seamless IAM Integration The beauty of ENSTO lies in its simplicity — it doesn’t demand a complete system overhaul. It integrates seamlessly with your existing IAM solution, adding powerful data protection without disrupting your workflows or user experience. Real-World Impact: How ENSTO Protects Enterprises Let’s bring this down to real-world scenarios. HR departments: Employee information stored in HR SaaS platforms stays safe even if the system gets breached. Finance teams: ENSTO ensures customer records remain unintelligible, shielding them from unauthorised access. Sales and marketing teams: Customer data stays protected, even during third-party integrations or data transfers. Beyond daily operations, ENSTO also helps enterprises stay ahead of compliance standards like GDPR, the Australian Privacy Act, and ISO 27001. And perhaps the biggest win — trust. When customers know their data is genuinely secure, your brand earns credibility that marketing alone can’t buy. The Future of Enterprise Identity Protection Identity management is evolving fast. We’ve moved from Identity 1.0 (basic access control) to Identity 2.0 (cloud IAM), and now we’re entering Identity 2.5 — the age of Privacy-First Identity Management. This new phase isn’t just about managing who logs in — it’s about ensuring that the data behind every login stays private and protected at all times. ENSTO represents this shift perfectly. It bridges the gap between traditional IAM systems and the next wave of secure, intelligent identity protection. So while others are still tightening their passwords, forward-thinking enterprises are already building privacy into their data — from the inside out. Conclusion: Experience Identity Protection Redefined Here’s the simple truth: IAMs manage access, but ENSTO protects what truly matters — the data itself. In a world where SaaS drives every business function and data breaches are a daily headline, your security strategy can’t stop at user authentication. You need a system that ensures your data remains safe, unreadable, and resilient — even when the unexpected happens. That’s what ENSTO delivers. Experience identity protection redefined with ENSTO — your safeguard for the SaaS-driven enterprise.
The data breach crisis in financial services has reached a tipping point. In 2024, the average cost of a breach in the financial sector hit $6.08 million, representing a 22% premium over other industries. But beyond these staggering numbers lies an even more troubling truth: most organisations are investing heavily in identity management solutions that deliver operational overhead with minimal customer value while missing the one element that truly matters-TRUST. For CIOs and CISOs leading financial institutions today, it’s time for a fundamental shift in how we approach identity security. The Operational Burden of Traditional Identity Management Most financial institutions today deploy a complex web of identity management solutions: Identity and Access Management (IAM), Privileged Access Management (PAM), and Identity Governance and Administration (IGA). While each plays a role in the security ecosystem, they share a common characteristic—they’re primarily operational tools that consume resources without directly boosting customer confidence. IAM manages user authentication and access controls across systems. It answers the question “who gets in?” by verifying identities and enforcing access policies. While essential for security hygiene, IAM requires constant maintenance, integration efforts with every new application, and significant administrative overhead. PAM goes further by securing privileged accounts—those administrator credentials that hold the keys to your most sensitive systems. It adds session monitoring, credential vaulting, and password rotation to protect against insider threats. Yet PAM deployment is notoriously complex, requiring specialised security controls for high-risk environments. IGA attempts to bring governance to the chaos by managing access rights, conducting periodic reviews, and ensuring compliance with regulations. Organisations report that time-consuming manual processes are the number one issue driving IGA investment, with over half finding that developing and maintaining custom connectors represents a significant burden. The reality? These systems represent substantial operational investments. Survey findings show that traditional IGA tools often cannot adapt easily to new cloud applications, leading to extensive custom coding. Administrative overhead remains high, implementation timelines stretch on, and organisations find themselves constantly playing catch-up. More critically, while these tools protect the institution’s perimeter, they do nothing to reassure customers that their data is safe when a breach occurs. They’re invisible to customers, creating no competitive differentiation and building zero customer trust (NOT to be mistaken with zero trust policy). Data Loss Prevention: The Only Segment That Touches Customers Among identity management segments, Data Loss Prevention (DLP) stands alone as the solution that directly impacts customer perception. Unlike IAM, PAM, and IGA—which operate behind the scenes—DLP actively protects customer data from unauthorised access, misuse, and exfiltration. DLP solutions monitor data in motion, at rest, and in use. They detect when sensitive information is being accessed inappropriately and can prevent data from leaving your organisation. Most importantly, when properly communicated, DLP demonstrates to customers that you’re actively protecting their information, not just controlling who can log in. The benefits are clear. DLP helps maintain customer trust by safeguarding sensitive information and demonstrating a commitment to data protection. In an era where consumers are increasingly concerned about privacy, this visible protection is essential for building and maintaining customer loyalty. Current DLP systems also have limitations. They cannot prevent data theft once systems are compromised. It cannot make stolen data unintelligible to attackers. And critically, it cannot turn the narrative after a breach from “we failed to protect you” to “your data remains secure even after the attack.” The Real Business Problem: Lost Trust Equals Lost Revenue Here’s what keeps financial executives awake at night: cyberattacks don’t just cost money in direct damages—they destroy the foundation of customer relationships. Research shows that 75% of customers would stop shopping with a brand after a security breach. More than 60% would avoid a company entirely following an incident. After suffering a breach involving personal financial data, the average firm loses 1.1% of its market value and experiences a 3.2 percentage point drop in year-on-year sales growth. Consider the ripple effects. Cisco’s 2017 research revealed that 38% of organisations experiencing breaches lost more than 20% of their revenue. Perhaps more damaging, 22% lost customers, with 40% seeing more than 20% of business slip away. Another 23% missed out on new business opportunities, with 42% losing 20% of prospective projects. The financial sector experiences these impacts acutely. As Jerome Powell, Chair of the Federal Reserve, stated: “Cyberattacks are now the foremost risk to the global financial system, even more so than the lending and liquidity risks that led to the 2008 financial crisis”. When customers trust you with their life savings, their mortgage, their retirement—that trust is everything. A breach shatters that relationship. Research on bank data breaches shows customers who had information compromised were significantly more likely to terminate their relationship with the bank in the six months following the event, even when fully compensated and suffering no monetary loss. The lack of attribution magnifies this effect. When banks cannot clearly explain what happened or trace fraud to a specific party, customer churn increases dramatically. Uncertainty becomes a significant source of lost loyalty. This isn’t just an IT issue—it’s a fundamental business problem that threatens long-term viability. Introducing Cyber Resilience: Turning Bad News Into Reassurance Traditional cybersecurity operates on a prevention model: build higher walls, add more locks, and monitor more carefully. But what happens when prevention fails? In today’s threat landscape, where attacks are inevitable, the question isn’t “if” but “when” you’ll face a breach. This is where cyber resilience changes the game. Rather than only preventing attacks, cyber resilience assumes compromise and ensures your organisation can maintain operations and protect customer data even after an intrusion occurs. For financial institutions, cyber resilience means the ability to adapt to disruptions caused by security incidents while maintaining continuous business operations. It’s the difference between telling customers “we were breached and your data may be compromised” versus “we were attacked, but your data remains protected.“ This mindset shift transforms how you communicate during a crisis. Instead of apologising for failure, you demonstrate strength. Instead of offering credit monitoring as consolation, you prove your architecture
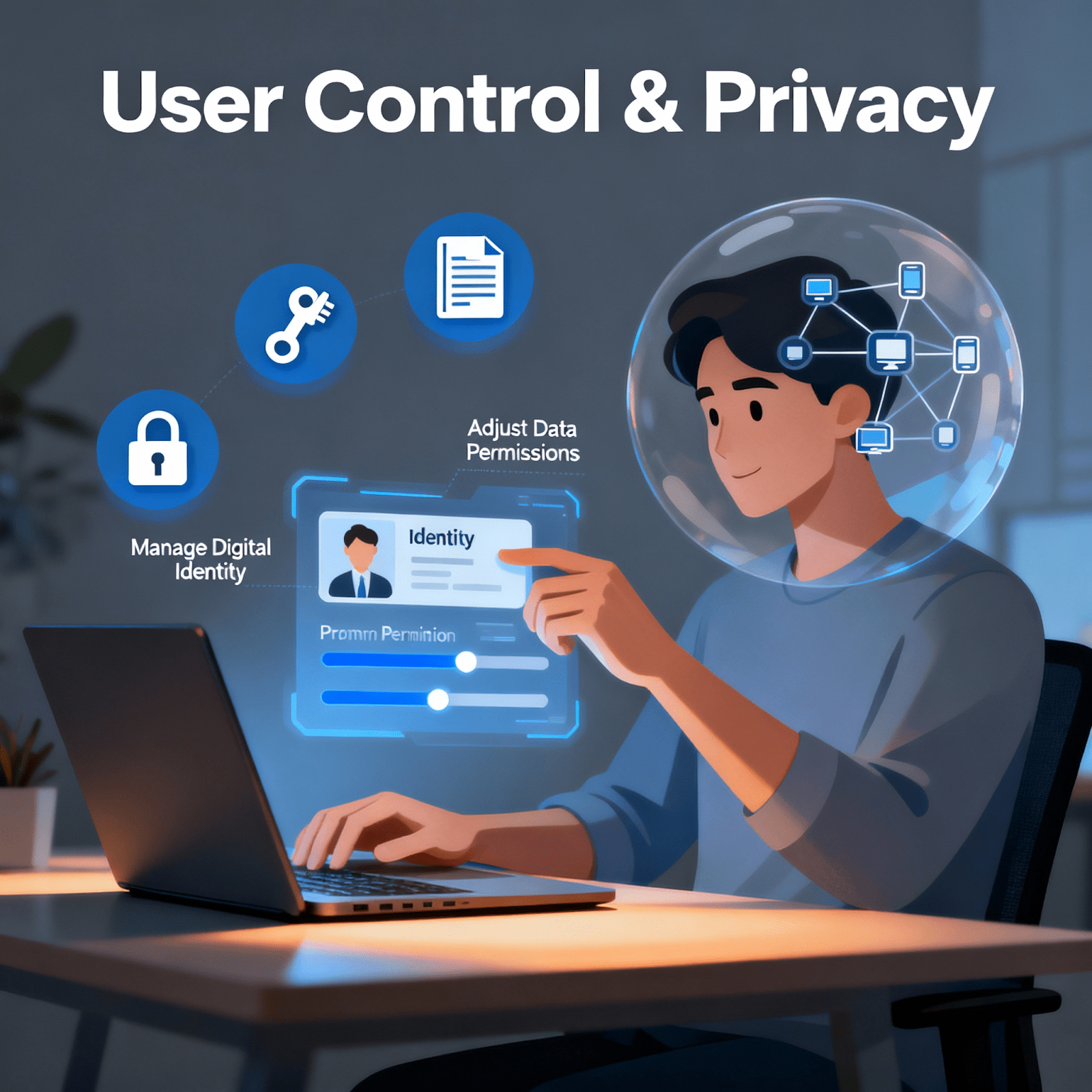
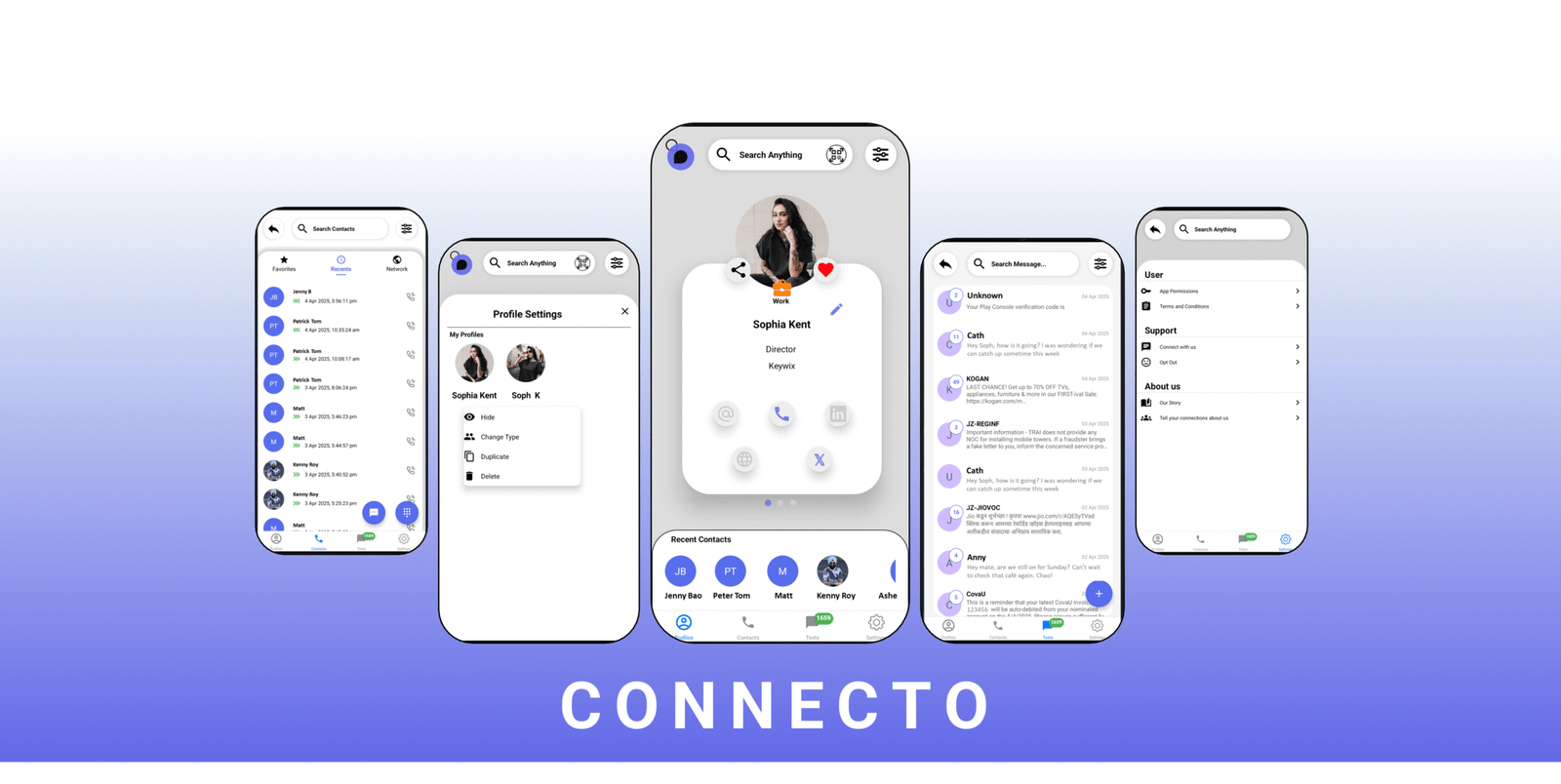
When your default phone app is simultaneously collecting your data, corporations are monetising your information, and hackers are getting bolder, it becomes clear that the way we manage digital identity has fundamentally broken. It’s time for a better approach. It’s time for Connecto. The Problem: Identity Has Become a Liability Every day, you unlock your phone and run dozens of apps. Most of them are doing something you may not realise: collecting data. Your phone number, call logs, SMS messages, and contact information—it’s all valuable to someone. Whether it’s marketers profiling your behaviour or criminals targeting your identity, your identity is treated as a commodity. The architecture of modern telecommunications was built in an era when privacy wasn’t even considered a feature. Your phone app and your contacts identify you with your phone number. Your messaging apps monitor your contacts. Third-party services track which businesses you contact and when. This isn’t paranoia—it’s reality. In fact, research shows that 89% of data breaches now involve compromised identities, making authentication and personal data control the most critical security issue facing individuals and organisations today. But the problem runs deeper than just data collection. Traditional identity management systems prioritise access first, asking for all your personal information upfront to grant you access to services. This means organisations collect mountains of data they don’t need and create massive, lightly-secured repositories that become honeypots for hackers. When one gets breached, millions of people suffer consequences they never consented to. The identity management industry has known this for years—yet nothing has changed, because the incentives weren’t aligned. Companies profited from data collection while users bore the risk. Then came Keywix – An IdentityAI Company, built on a revolutionary principle: privacy-first architecture where privacy and user control come before everything else. The Evolution of Identity: From Share-Everything to User-Controlled Systems To understand why Connecto represents a genuine breakthrough, it helps to understand how we got here. Digital identity hasn’t always been this messy. In the early days of the internet (circa late 1990s), identity management was simple—a username and password. Basic, but vulnerable. As cyber threats escalated, the industry layered on complexity: two-factor authentication, biometrics, and security questions. Each innovation added friction while marginally improving security. Organisations deployed more sophisticated systems like Single Sign-On (SSO) and federated identity management, allowing users to authenticate once across multiple services. However, these systems all share a common flaw: they’re built on the assumption that businesses should control and govern your identity data with bare minimum privacy parameters. This paradigm has produced today’s disastrous results. The evolution looks something like this: Identity 1.0 (Late 1990s – Early 2000s): Basic usernames and passwords. Vulnerable to brute force attacks. Users managed dozens of credentials manually. Identity 2.0 (2000s – Today): Multi-factor authentication, third-party identity management platforms (Okta, Azure AD), and federated systems. Better security, but still vulnerable to data duplication. What Makes Connecto Different: The Identity-First Approach Connecto isn’t just another communications app. It represents a fundamentally different philosophy about who controls your digital identity. Here’s what makes it revolutionary: 1. Your Data Never Leaves Your Phone This isn’t a marketing pitch—it’s architectural. Every call, every text, every piece of personal information stays on your device. There is no cloud synchronisation of your messages or calls. The only people who can access your communications are you and the people you explicitly choose to communicate with. For businesses, this means you’re not subject to organisational data loss. For individuals, it means you’re not feeding a surveillance machine simply to make phone calls. 2. Hide Your Number, Control Your Identity One of Connecto‘s most powerful features addresses a real problem: sometimes you don’t want to give someone your real phone number. Maybe you’re a small business owner networking with vendors. Maybe you’re arranging a pickup with a stranger. Maybe you’re simply protective of your personal contact information. Traditional phone apps don’t give you this choice—they expose your number by default. Connecto inverts this paradigm. You can hide your number from any contact or all contacts. The person can still reach you, they can still communicate with you, but they don’t get access to your permanent identifier. This is a seemingly small feature with profound implications: it’s the difference between companies managing your identity and you managing it yourself. 3. Digital Business Cards That Actually Respect Privacy Most digital business card apps work like this: you upload your information to their cloud service, they generate a QR code hosted on their servers, and anyone can access your card via the internet connection. This uploads your professional identity to yet another database vulnerable to breaches. Connecto’s approach: your business card lives on your phone, encrypted, under your control. You can share it via QR code without requiring the recipient to install an app or connect to the internet. The card can include photos, social media links, and your aesthetic. You can even create multiple versions—one for investors, one for friends, one for business contacts—and control exactly what each audience sees. For entrepreneurs and salespeople, this is genuinely transformative. It means you can establish a professional presence without building someone else’s user database. 5. Privacy Modes for Different Contexts Humans have different identities for different contexts. You’re one person at work, another with close friends, another when handling personal business. Most phone apps force you into a single identity. Connecto allows you to create multiple privacy modes and switch between them. This means you can compartmentalise your identity appropriately—protecting different aspects of yourself for different relationships and situations. Why Businesses Should Care: Privacy-First is Business-First If you’re running a company, you’ve probably already heard about the costs of identity-related breaches. The average data breach now costs organisations $4.88 million, and breaches involving compromised credentials take an average of 328 days to identify and contain. But there’s a deeper business case for identity-first systems like Connecto: Reduced Compliance Burden Traditional communications systems create compliance headaches. Your company probably has policies requiring you to use corporate phone
In a time when nearly every app wants a slice of your personal data, Connecto promises something increasingly rare: genuine privacy-first communication without data collection or third-party sharing. Available on Google Play as a privacy-first phone and SMS app, Connecto makes a bold claim: “Your data never leaves your phone, seriously, never.” That’s a refreshingly straightforward statement in an era where even apps claiming to be “secure” have been caught quietly sharing data with analytics platforms, advertisers, and third-party services. So the real question isn’t whether Connecto sounds good—it’s whether the technology actually delivers on that promise. Let’s dig into it. What Connecto Actually Offers & How It Works Connecto replaces your default dialer and SMS app with a privacy-first communications platform built on a simple premise: encryption at source, no server storage, no data harvesting. The app comes with these core features: End-to-end encryption for calls and texts using existing GSM network infrastructure, ensuring that communications remain private from endpoint to endpoint. Number hiding capabilities, allowing you to mask your real number when calling unknown contacts or all contacts—a feature that addresses a real gap in mainstream communication apps. Digital contact cards that you design, share via QR code, and update in real-time—giving you granular control over which information you share with whom. Full integration as your default dialer and SMS handler, replacing your standard phone app entirely. In practice, this means Connecto completely takes over as your dialer and messenger, functioning exactly like your current phone app but with added privacy architecture fundamentally different from mainstream alternatives. The Privacy Claims: What’s Actually Verifiable According to Connecto’s Google Play Data Safety section, the app: Does NOT share data with third parties. Does NOT collect data for analytics, advertising, or any other purpose. These are genuinely rare claims. Keywix provides detailed documentation outlining how encryption, permissions, and identity verification operate locally on your device, with everything staying encrypted on your phone. Permissions, Architecture & Legitimate Concerns For any app replacing your dialer and messaging system, certain permissions are unavoidable: contacts, call logs, microphone, and SMS access are fundamentally required. That’s not automatically a red flag. The relevant question is how responsibly and transparently an app handles that access. Connecto’s architecture claims suggest that all processing happens locally, which addresses the fundamental issue that drives privacy concerns. Centralised data creates honeypots—if 60% of enterprise SaaS applications duplicate identity data across multiple systems, consumer apps similarly consolidate contact and communication records, creating concentrated targets for attackers. However, skepticism is warranted in several areas: Digital contact card: If contact cards update “anytime,” that inherently suggests some form of data transmission. Keywix claims this happens securely, but the mechanism deserves transparency. Are updates end-to-end encrypted? What servers, if any, facilitate synchronisation? Number hiding implementation: GSM networks obviously know which number is calling. Connecto’s number-hiding feature must work through some mechanism—likely involving call forwarding or network-level routing through privacy infrastructure. Understanding exactly how this works would strengthen confidence in the implementation. These aren’t criticisms of Connecto—they’re genuine architectural questions that legitimate privacy advocates should ask about any communication platform. Real-World Usage Data: Limited but Promising With an approximate number of currently downloads in low 100s, Connecto doesn’t yet have sufficient user volume to provide definitive long-term safety data. What early users report on the Play Store is encouraging: Smooth, minimal experience that appeals to privacy-conscious users tired of bloated, feature-heavy communication apps. Number-hiding and spam-blocking features work as expected, with early users noting practical effectiveness. Expected minor bugs for a newer application, but importantly, no privacy-related complaints or data concerns in user feedback. However, this small sample size carries obvious limitations. You can’t meaningfully assess privacy practices or security vulnerabilities until an application has thousands of active users and multiple years of operational history. Connecto is still building this track record. The absence of privacy complaints isn’t definitive proof of safety—it reflects limited visibility into the platform rather than confirmed security. This is why third-party security audits and broader user adoption become critical markers of genuine trustworthiness. Comparison with Established Privacy Apps Let’s honestly assess how Connecto stacks against mature privacy-first platforms: Feature Connecto Signal Telegram WhatsApp End-to-End Encryption ✅ ✅ ✅ (Secret Chats) ✅ No Server Data Storage ✅ ⚠️ ⚠️ ❌ Number Hiding ✅ ❌ ❌ ❌ AI Spam Blocking ✅ ❌ ❌ ❌ Open Source Partial ✅ ✅ ❌ Independent Security Audits Limited ✅ ✅ ✅ User Base Size ~200 Millions Millions Billions Years of Proven Security <1 year 10+ years 10+ years 15+ years Connecto’s distinctive advantages are clear: true zero-server architecture and identity protection features that neither Signal nor other mainstream alternatives offer. Signal has better open-source transparency and a longer operational history. Telegram has massive user adoption but maintains server-side data. The honest comparison? Connecto is genuinely innovative on features, but it’s simultaneously unproven on security. The Broader Context: Connecto Within Keywix’s Privacy-First Ecosystem Understanding Connecto requires context about its parent company Keywix. Connecto is the consumer-facing component of a larger privacy-first identity ecosystem that includes Ensto, an enterprise platform built on patent-pending technology for fragmentation, encryption, and distributed identity protection. This matters because Connecto isn’t a standalone experimental app—it’s part of a deliberate product strategy. Keywix’s approach to protecting identity data through unintelligible fragmentation and encryption directly informs Connecto’s architecture. The company has provisional patents granted and is currently running enterprise pilots with established organisations. This context supports confidence in Connecto’s architecture while not eliminating the need for cautious optimism about unproven consumer-scale deployment. The Honest Verdict: Is Connecto Safe to Use? The straightforward answer: Connecto appears to be genuinely built around privacy-first principles, but calling it “proven safe” requires further evidence. What gives confidence: ✅ Authentic privacy-first architecture rather than privacy as an afterthought—Connecto genuinely doesn’t collect data or share with third parties. ✅ Backed by founders with genuine identity and cybersecurity expertise—Keywix co-founders have 14+ years in identity management and authentication systems, not just app development. ✅ Integration with patent-pending privacy technology rather than generic
Why Every Business Leader Must Act Now Skip to the topics most critical for your business: Discover the escalating threat landscape – Learn how 1,113 data breaches in Australia alone during 2024 are costing businesses millions and endangering customer trust. Understand the real business impact – See why healthcare breaches now cost $9.77 million per incident, while financial services face 27% of all global breaches. Explore Keywix’s IdentityAI – Learn how this privacy-first platform eliminates data harvesting risks while providing enterprise-grade communication tools. See the eight-week transformation plan – Get actionable steps for implementing user-controlled identity across your organisation’s communication channels. Calculate your protection ROI – Understand how proactive identity management delivers measurable returns compared to post-breach recovery costs. The $4.44 Million Wake-Up Call: Why Data Breaches Are Every CIO’s Nightmare The statistics are staggering and getting worse. In 2024, businesses globally faced an average data breach cost of $4.44 million, with some sectors experiencing far higher losses. Australian organisations alone reported 1,113 data breaches in 2024, representing a 25% increase from the previous year. But these numbers only tell part of the story. The Hidden Costs Beyond the Headlines When a major airline recently experienced a data breach affecting over 5 million customers, the immediate fallout went far beyond the initial security incident. Customer trust evaporated overnight, operational systems required a complete overhaul, and regulatory penalties mounted quickly. The real damage wasn’t just the stolen data—it was the months of customer service calls, system rebuilds, and reputation management. Healthcare organisations face the steepest financial impact, with breaches averaging $9.77 million per incident. One major health insurer’s breach exposed 12.9 million Australians’ personal information, including Medicare numbers and prescription details. Financial services aren’t far behind, with the sector now accounting for 27% of all global breaches. Why Traditional Security Isn’t Working The problem isn’t just external threats. Human error contributes to 60% of all breaches, while third-party vulnerabilities account for another significant portion. Traditional security models assume data will be distributed amongst several SaaS systems and protected by perimeter defences. But modern business reality involves remote work, legacy systems, cloud services, and countless third-party integrations—each creating potential weak points. A major construction company recently lost 350GB of data, including employee records and engineering documents. The breach occurred not because their security was weak, but because their approach was fundamentally outdated. They were protecting castles in an age of mobile armies. The Privacy-First Revolution: How Smart Organisations Are Fighting Back The most successful organisations aren’t just building higher walls—they’re rethinking the entire approach to data protection through privacy-first architecture. This means putting user control at the centre of every data decision, rather than hoping systems built to duplicate user data will keep information safe. Keywix: The Business Case for Privacy-First Communication Keywix eliminates the costly cycle of data duplication across your software stack. Instead of maintaining user information in dozens of different platforms—each creating another security vulnerability and compliance headache—organisations can centralise communication through a single privacy-first platform. This approach transforms scattered data liabilities into a unified, user-controlled asset, dramatically reducing your attack surface while simplifying regulatory compliance and cutting IT management overhead. The business impact is immediate: IT teams stop managing user data across multiple systems, compliance teams get automatic audit trails, and security teams monitor one communication channel instead of dozens. Most importantly, when users control their own data sharing, your organisation eliminates the legal and financial exposure that comes from storing customer information you don’t actually need to hold. The Eight-Week Implementation Framework Week 1: Assessment Phase Evaluate current communication vulnerabilities and data exposure points. Most organisations discover they have user data scattered across dozens of systems they weren’t fully aware of. Week 2: Pilot User Group Begin with executive communications and high-value targets. These users typically handle the most sensitive information and benefit most from enhanced protection. Week 3-4: First-Department Rollout Expand to one or more departments handling sensitive data—HR, Finance, Ops. These groups immediately understand the value of user-controlled communication. Week 4-6: Pilot External Communication Implement for customer and vendor communications. This is where organisations often see the biggest immediate risk reduction. Week 6-7: Integration Planning Connect with existing business systems through secure APIs, maintaining the privacy-first approach throughout. Week 8: Training and Adoption Roll out user training focused on the business benefits rather than technical features. Users who understand why they’re in control adopt faster. The Dark Web Reality: Why Your Customer Data Is Already at Risk The most sobering reality facing business leaders today is that customer data breaches aren’t just possible—they’re probable. Recent analysis of dark web marketplaces shows stolen identity information from healthcare providers, airlines, and financial institutions being sold within hours of major breaches. The Multiplication Effect of Data Breaches When customer information appears on the dark web, the damage multiplies exponentially. A single breach doesn’t just affect the original organisation—it enables fraud across the entire digital ecosystem. Customers whose airline frequent flyer data was stolen find themselves targeted by sophisticated phishing attacks months later, using their personal details to create convincing fake communications. Financial services face particularly severe consequences. Banking data breaches provide criminals with everything needed for account takeovers, fraudulent transactions, and identity theft. The stolen information isn’t just used once—it becomes part of criminal databases used for years of ongoing fraud. The Enterprise Security Ecosystem: How Keywix Integrates Smart organisations understand that security tools must work together seamlessly. Keywix’s privacy-first architecture integrates naturally with existing enterprise security investments rather than requiring wholesale replacement of current systems. Seamless Integration Points Identity Management Systems: Connecto works alongside existing IAM platforms by providing the communication layer that respects user identity controls. Instead of bypassing existing identity systems, it extends them into communication workflows. SaaS, Security Information and Event Management (SIEM): While Keywix reduces the amount of security data that needs monitoring, it integrates with SaaS and SIEM systems to provide visibility into communication patterns without compromising user privacy. Compliance Management: Connecto’s user-controlled data model automatically
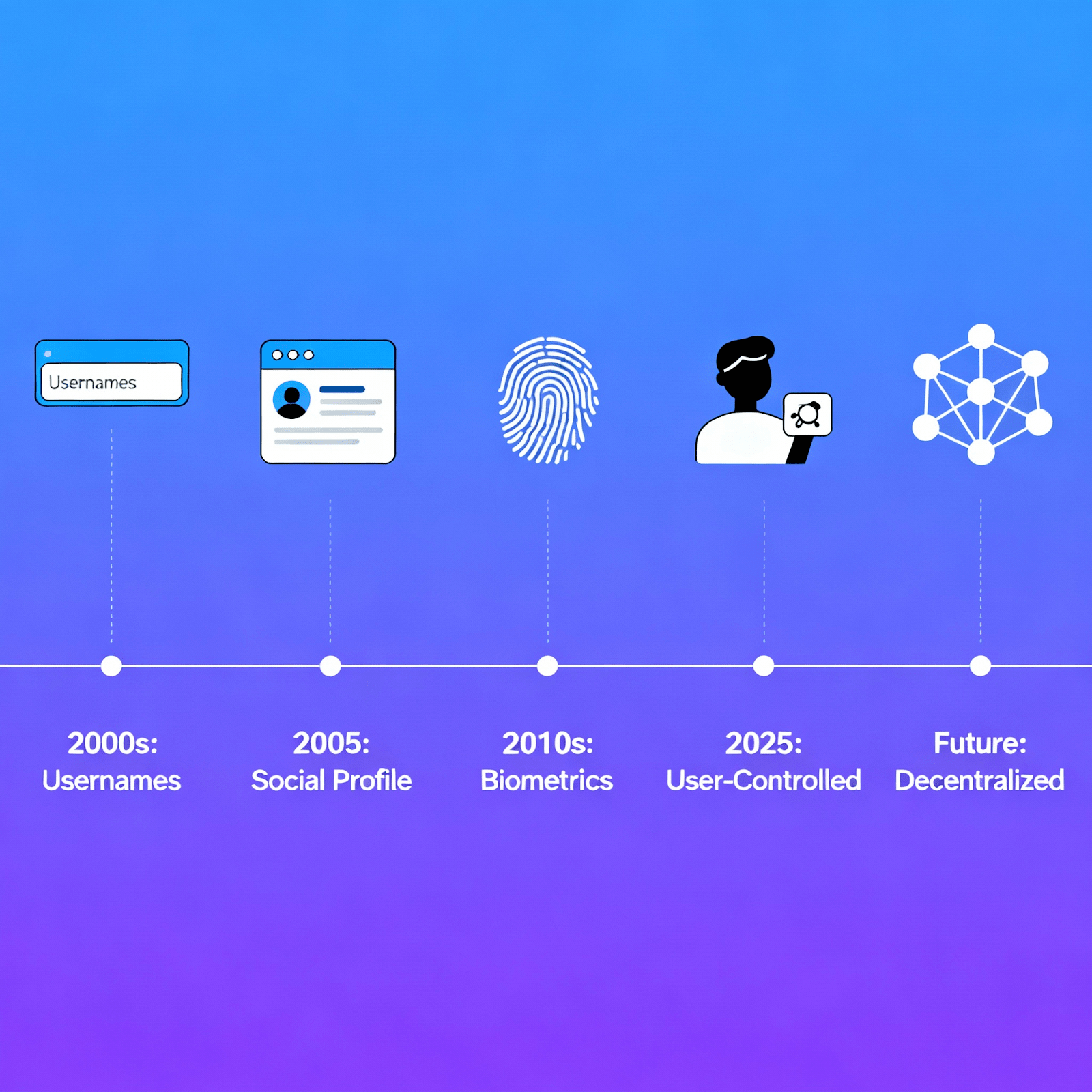
TL;DR Connecto by Keywix transforms everyday communication for both privacy-focused individuals and enterprise security teams. With end-to-end encryption, on-device data storage, and granular privacy controls, Connecto empowers users with true data sovereignty. In an age where personal data is commoditised and corporate systems face ever-escalating security threats, the need for privacy-first solutions has never been greater. Connecto replaces traditional phone and messaging apps with a unified platform that ensures: Zero data harvesting End-to-end encrypted calls and messages On-device storage of all personal and business data Multiple privacy modes for different contexts This deep dive explores Connecto’s capabilities for both end users and businesses, tracing the evolution of digital identity, reviewing Connecto’s key features, and illustrating how this app sets a new standard for trust, control, and compliance. The Evolution of Digital Identity Digital identity has progressed through several distinct phases: Identity 1.0 (Username & Password): Introduced in the 1960s, basic authentication relied on usernames and passwords stored in institutional databases. This approach provided convenience but centralised vast user data, creating high-value targets for attackers. Identity 2.0 (Social Login & SSO): The rise of social networks and single sign-on streamlined access across services but encouraged oversharing and introduced third-party dependencies. Identity 2.5 (User-Controlled Identity): Emerging today, this paradigm returns control to individuals via on-device storage and consent-driven data sharing, embodied by Keywix’s “Applications over Information” principle. Identity 3.0 (SSI & Decentralised Credentials): Looking ahead, self-sovereign identity on distributed ledgers promises privacy-preserving, tamper-resistant credentials under users’ direct control. Connecto for Privacy-Focused End Users 1. Robust Privacy by Design Most communication apps are either too siloed with factory settings or monetise user metadata. Connecto abolishes trackers and telemetry: User-Controlled Data Storage: Call logs, messages, and digital cards never leave the device. End-to-End Encryption: Both voice and text are GSM-enabled, preventing eavesdropping. Ghost Mode: Hide your number selectively to unknown or all contacts, blocking spam at the source. 2. Seamless Migration from Default Apps Switching to Connecto is effortless: It auto-configures as your default phone and SMS handler. Customisable notifications and thread-based messaging maintain familiarity. Multiple privacy modes adapt to personal, social, or professional scenarios. 3. Next-Generation Contact Sharing Traditional digital business cards rely on third-party clouds. Connecto’s solution: Free Digital Contact Cards: Design and update live on your device. QR Code Sharing: Recipients scan without needing the app or a cloud account. Instant Updates: Card details will soon refresh in real time on other devices. Connecto on Google Play: Key Features & User Feedback The Connecto app delivers a full suite of privacy-first communication tools in one package: Hide your number selectively (Ghost Mode) Advanced caller ID Multiple privacy modes for flexible sharing GSM-enabled calls and texts Customizable digital contact cards with QR codes Users praise Connecto as a zero-data-harvesting alternative to default phone apps and messaging services, earning strong ratings for privacy, ease of use, and security. Keywix for Businesses: Unified Identity Management The Challenge: Fragmented Identity Data Enterprises often duplicate customer identity data across dozens of systems, expanding their attack surface and complicating compliance. Key statistics: Average enterprise spans 25+ identity repositories across SaaS and legacy apps. OAIC reported 1,113 data breach notifications in Australia in 2024, up 25% year-over-year. Phishing and credential theft remain top threat vectors. Keywix’s Business-Ready Capabilities Keywix extends beyond consumer communication to enterprise identity governance: IdentityAI-Powered Analytics: Real-time insights into identity usage and risk via an intuitive dashboard. SCIM Integration: Automated provisioning and deprovisioning across platforms, eliminating orphaned accounts. Tokenisation & Zero-Knowledge Access: Share tokenised identifiers with internal systems, keeping PII secure. Audit-Ready Logs: Timestamped records of all identity events for regulatory reporting. Real-World Impact Faster Onboarding: Provision thousands of users overnight via SCIM sync. Instant Offboarding: Deactivate accounts across all systems in seconds to minimise risk. Tenant Mergers: Harmonise identities during restructures without manual scripts. Benefits of Keywix’s “Applications over Information” Philosophy Data Minimisation: Only allow users to act and not view users’ information, only when it’s needed. User-Controlled: Individuals take control over data exposed to organisations. Regulatory Alignment: Privacy-first architecture supports modern data protection laws. Scalable Security: Adapt personal chats to enterprise communications, without compromising confidentiality. Conclusion: Embrace the Future of Secure Communication Connecto by Keywix is set to hit a new benchmark for privacy and identity management—empowering individual users to reclaim their data while equipping businesses with automated, compliant identity workflows. Whether you seek true data control in everyday calls and texts, or you need robust identity governance across complex enterprise environments, Keywix delivers a cohesive solution. Download Connecto on Google Play today and experience the next generation of privacy-first communication.
TL;DR: Connecto by Keywix combines a privacy-first design with IdentityAI features to offer both individual users and businesses a unified communication and identity management solution that keeps data on-device, enforces end-to-end encryption, and streamlines secure connections. Download NOW to see for yourself! Introduction: Why Privacy and Control Matter Today In an era where over 2.2 billion user records have been compromised by cyberattacks, digital privacy is no longer optional—it’s essential. Consumers demand apps that respect their data, while enterprises need robust identity governance to comply with regulations and reduce security risks. Connecto addresses these twin imperatives by offering an integrated phone and messaging app built on user-controlled identity principles, ensuring that personal and corporate data never leaves the device without explicit user consent. Evolution of Digital Identity: From Mindless Sharing to User-Controlled The journey of digital identity began with simple username-and-password schemes in the 1960s, evolving through institutional databases and public key infrastructure (PKI) to social login and single sign-on solutions. However, mass sharing led to massive data breaches and privacy violations. Today, user-controlled identity empowers users to control their identifiers without relying on a single authority. Generational Changes in Identity Management: Identity 1.0 (Credit Bureau Era): Username/password and credit histories for verification. Identity 2.0 (Social Login & SSO): Convenience but oversharing and unsecured data aggregation. Identity 2.5 (User-Controlled Identity Management): This is where we are. Allowing users to control their personal information with the ‘Applications over Information’ principle. Identity 3.0 (SSI & DCI – Future): Privacy-preserving, user-controlled credentials on distributed ledgers. Introducing Connecto: Privacy-First Communication Connecto reimagines your phone’s core functions—calls and messages—through a privacy-centric lens. Built by Keywix’s patent-pending identity technology, it offers: End-to-End Encryption for both calls and texts, ensuring no intermediaries can access your communications. On-Device Data Storage: Your call logs, contact cards, and message history never leave your phone. Ghost Mode: Hide your number selectively, blocking spam and unknown callers with advanced filtering. Free Digital Contact Cards: Design and share via QR codes without storing data on external servers. The result: a seamless replacement for your default dialer and SMS apps—no subscriptions, no data harvesting. Targeting Privacy-Focused End Users 1. Security You Can Trust For individuals wary of surveillance, Connecto provides zero telemetry. By never sending metadata to third parties, it eliminates the risk of profiling and data resale. Advanced spam blocking leverages on-device AI, stopping unwanted calls before your phone even rings. 2. Seamless User Experience Switching to Connecto is effortless: it automatically integrates as your default phone and messaging handler. Customizable notifications and thread-based messaging make communication intuitive, while multiple privacy modes let you adapt settings for work, personal, or public scenarios. 3. Next-Gen Contact Sharing Traditional digital business cards often store your data in proprietary clouds. Connecto’s contact cards live solely on your device, updating live and sharing via QR codes—recipients don’t need the app to scan or store your information. Conclusion: Embrace Privacy-First Communication Today Connecto represents a paradigm shift—a unified app that respects user sovereignty, delivers enterprise-grade identity management, and preserves the simplicity of everyday communication. Whether you’re an individual seeking true privacy or a business aiming for secure, compliant workflows, Connecto is ready to transform how you connect, call, and collaborate. Download Connecto on Google Play and experience communication that puts you in control.
Learn how the Privacy-First approach enhances Digital Identity Security and builds safer, more trustworthy communications in the digital era. Digital identity isn’t just changing how we authenticate ourselves online—it’s fundamentally altering the fabric of human connection and business operations. As 94 million data records were leaked in just the second quarter of 2025, and 45% of global organisations are predicted to face software supply chain attacks by the end of 2025, we’re witnessing an unprecedented crisis of digital trust that demands immediate attention. The statistics paint a stark picture of our vulnerability. The global average cost of a data breach has reached $4.88 million, representing a 10% year-over-year increase that shows no signs of slowing. More troubling still, organisations now take an average of 241 days to detect and contain a data breach, meaning most companies remain unaware of compromises for over eight months. The Hidden Costs of Digital Communication What many don’t realise is that our everyday communication tools have become sophisticated data harvesting operations. Online caller information and messaging apps collect and analyse user data to monetise their services, creating significant privacy concerns. This includes harvesting user conversations, metadata, and personal information that’s often sold to third parties without explicit user consent. The business implications are staggering. When WhatsApp was introduced for corporate communications, organisations lost control over employee information privacy, leading to unmonitored sharing of sensitive information and increased risk of data leaks. The platform’s open nature means users cannot prevent hackers from contacting them, making it a common vector for malware distribution. The Real Price of “Free” Communication Consider the hidden economics of popular messaging platforms: Data harvesting operations create detailed user profiles sold to advertisers and data brokers Targeted advertising systems reveal how much these platforms know about users’ personal lives Uncontrolled data sharing means personal information can be further sold, shared, or leaked beyond platform control Jeff Bezos was hacked through a WhatsApp video message in January 2020, demonstrating that even the world’s wealthiest individuals aren’t immune to these vulnerabilities. Similarly, a spyware vendor successfully compromised 1,400 devices through WhatsApp, leading to a lawsuit from Facebook. Emerging Trends Reshaping Privacy in Communications Privacy-first communication models are becoming essential for regulatory compliance. New regulations like eIDAS 2.0 and the NIS2 directive require organisations to better secure their digital systems and enhance cyber resilience. These regulatory changes are driving increased adoption of solutions that minimise personal data collection while ensuring users maintain complete control over information usage. The Business Impact: Beyond Financial Loss Identity theft affects far more than immediate financial costs. For businesses, the implications cascade through multiple operational areas: Operational Disruption and Resource Drain Identity theft victims spend roughly 100-200 hours (12.5 to 25 workdays) to undo the damage. This represents a massive drain on employee productivity and organisational resources. Remediation efforts include investigating breaches, implementing security measures, and restoring affected systems, consuming valuable time and resources that could otherwise drive business growth. Reputation and Customer Trust When businesses experience identity theft, customers, suppliers, and commercial partners may perceive the organisation as insecure. This perception leads to questions about whether the business’s information security controls can be trusted, potentially resulting in lost market share and revenue. Rebuilding trust with customers is a challenging and time-consuming process. A business’s reputation takes years to build but can be shattered instantly due to an identity theft incident. Consumers are increasingly concerned about data privacy and security, and failures to protect customer data can cause irreparable reputational damage. Financial and Legal Consequences Beyond direct financial losses, businesses face: Regulatory fines and penalties for non-compliance with data protection laws Lawsuits from affected customers and employees Increased IT costs to enhance security systems and monitor for threats Impacted credit scores that make future financing more difficult A Case Study in Digital Vulnerability U.S. companies identified 1,732 data breaches in just the first half of 2025, while European Union member countries noted 11,079 cyberattack events between July 2023 and June 2024. The scale of these incidents demonstrates that no region is immune to digital identity threats. CyberCX’s 2025 Threat Report revealed that business email compromise remained the top incident type, with 75% of BEC attacks involving attackers bypassing multi-factor authentication. Even more concerning, espionage incidents are going unnoticed for longer, with the average time to detect rising to more than 400 days. Healthcare was the most impacted sector, followed by financial services, highlighting how critical infrastructure and sensitive data repositories remain primary targets for identity-based attacks. A Paradigm Shift: Privacy-First Communication The solution isn’t to abandon digital communication—it’s to fundamentally reimagine how these systems operate. ‘Application over Information’ architecture ensures that privacy is embedded at the foundation, not patched on as an afterthought. This principle is beginning to take tangible shape through solutions such as the Connecto mobile app by Keywix, which demonstrates how calls, texts, and even the exchange of business cards can occur seamlessly without exposing or writing down personal details. By shifting control of identity and communication back to the user, privacy-first design establishes sovereignty for individuals and organisations while adapting to new security challenges. The Privacy-First Advantage Rethinking communication around privacy produces several systemic benefits: Zero personal data harvesting ensures information stays with the user End-to-end encryption protects calls, messages, and data sharing from intrusions Regulatory alignment is woven into architecture rather than applied reactively Networking functions—such as secure messaging and card sharing—expand without compromising confidentiality Real-World Implementation Privacy-first solutions are beginning to address many of the pain points in today’s digital exchanges. For Individuals: Privacy is enhanced without reducing usability or the convenience of mobile-native communication Caller ID protection and robust spam filtering secure personal identity layers Data sovereignty is strengthened with direct user control over what is shared, when, and with whom New forms of networking—like Connecto’s privacy-preserving card exchange—enable professional interaction without oversharing For Businesses: Compliance readiness evolves as regulation becomes more demanding around identity data Streamlined identity management supports digital transformation with reduced risk IdentityAI architecture resists emerging threats such as synthetic