Revolutionising Digital Identity: How the Privacy-First principle is Building Safer Communications Today
Learn how the Privacy-First approach enhances Digital Identity Security and builds safer, more trustworthy communications in the digital era.
Digital identity isn’t just changing how we authenticate ourselves online—it’s fundamentally altering the fabric of human connection and business operations. As 94 million data records were leaked in just the second quarter of 2025, and 45% of global organisations are predicted to face software supply chain attacks by the end of 2025, we’re witnessing an unprecedented crisis of digital trust that demands immediate attention.
The statistics paint a stark picture of our vulnerability. The global average cost of a data breach has reached $4.88 million, representing a 10% year-over-year increase that shows no signs of slowing. More troubling still, organisations now take an average of 241 days to detect and contain a data breach, meaning most companies remain unaware of compromises for over eight months.
The Hidden Costs of Digital Communication
What many don’t realise is that our everyday communication tools have become sophisticated data harvesting operations. Online caller information and messaging apps collect and analyse user data to monetise their services, creating significant privacy concerns. This includes harvesting user conversations, metadata, and personal information that’s often sold to third parties without explicit user consent.
The business implications are staggering. When WhatsApp was introduced for corporate communications, organisations lost control over employee information privacy, leading to unmonitored sharing of sensitive information and increased risk of data leaks. The platform’s open nature means users cannot prevent hackers from contacting them, making it a common vector for malware distribution.
The Real Price of “Free” Communication
Consider the hidden economics of popular messaging platforms:
- Data harvesting operations create detailed user profiles sold to advertisers and data brokers
- Targeted advertising systems reveal how much these platforms know about users’ personal lives
- Uncontrolled data sharing means personal information can be further sold, shared, or leaked beyond platform control
Jeff Bezos was hacked through a WhatsApp video message in January 2020, demonstrating that even the world’s wealthiest individuals aren’t immune to these vulnerabilities. Similarly, a spyware vendor successfully compromised 1,400 devices through WhatsApp, leading to a lawsuit from Facebook.

Emerging Trends Reshaping Privacy in Communications
Privacy-first communication models are becoming essential for regulatory compliance. New regulations like eIDAS 2.0 and the NIS2 directive require organisations to better secure their digital systems and enhance cyber resilience. These regulatory changes are driving increased adoption of solutions that minimise personal data collection while ensuring users maintain complete control over information usage.
The Business Impact: Beyond Financial Loss
Identity theft affects far more than immediate financial costs. For businesses, the implications cascade through multiple operational areas:
Operational Disruption and Resource Drain
Identity theft victims spend roughly 100-200 hours (12.5 to 25 workdays) to undo the damage. This represents a massive drain on employee productivity and organisational resources. Remediation efforts include investigating breaches, implementing security measures, and restoring affected systems, consuming valuable time and resources that could otherwise drive business growth.
Reputation and Customer Trust
When businesses experience identity theft, customers, suppliers, and commercial partners may perceive the organisation as insecure. This perception leads to questions about whether the business’s information security controls can be trusted, potentially resulting in lost market share and revenue.
Rebuilding trust with customers is a challenging and time-consuming process. A business’s reputation takes years to build but can be shattered instantly due to an identity theft incident. Consumers are increasingly concerned about data privacy and security, and failures to protect customer data can cause irreparable reputational damage.
Financial and Legal Consequences
Beyond direct financial losses, businesses face:
- Regulatory fines and penalties for non-compliance with data protection laws
- Lawsuits from affected customers and employees
- Increased IT costs to enhance security systems and monitor for threats
- Impacted credit scores that make future financing more difficult
A Case Study in Digital Vulnerability
U.S. companies identified 1,732 data breaches in just the first half of 2025, while European Union member countries noted 11,079 cyberattack events between July 2023 and June 2024. The scale of these incidents demonstrates that no region is immune to digital identity threats.
CyberCX’s 2025 Threat Report revealed that business email compromise remained the top incident type, with 75% of BEC attacks involving attackers bypassing multi-factor authentication. Even more concerning, espionage incidents are going unnoticed for longer, with the average time to detect rising to more than 400 days.
Healthcare was the most impacted sector, followed by financial services, highlighting how critical infrastructure and sensitive data repositories remain primary targets for identity-based attacks.
A Paradigm Shift: Privacy-First Communication
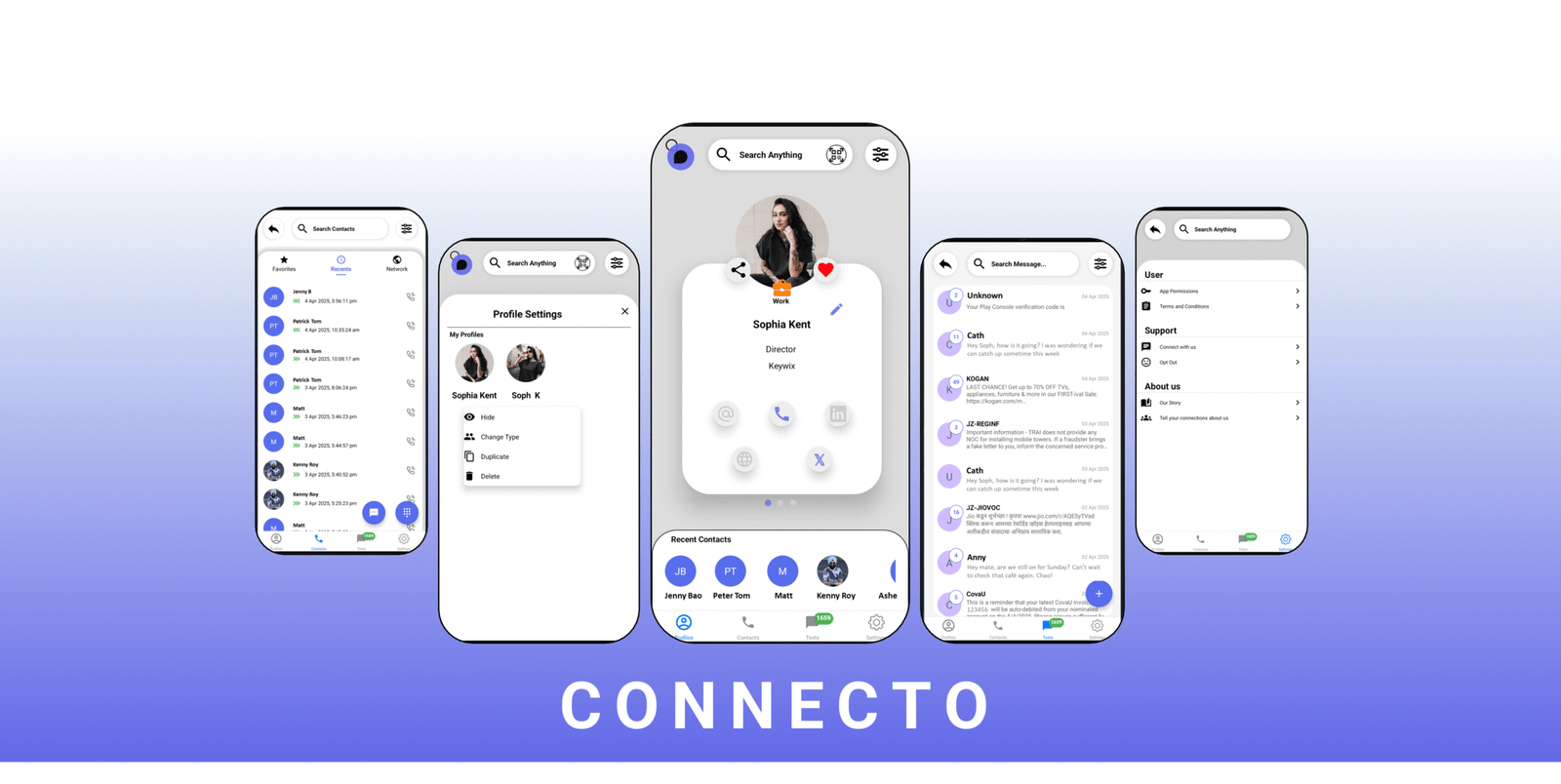
The solution isn’t to abandon digital communication—it’s to fundamentally reimagine how these systems operate. ‘Application over Information’ architecture ensures that privacy is embedded at the foundation, not patched on as an afterthought. This principle is beginning to take tangible shape through solutions such as the Connecto mobile app by Keywix, which demonstrates how calls, texts, and even the exchange of business cards can occur seamlessly without exposing or writing down personal details. By shifting control of identity and communication back to the user, privacy-first design establishes sovereignty for individuals and organisations while adapting to new security challenges.
The Privacy-First Advantage
Rethinking communication around privacy produces several systemic benefits:
- Zero personal data harvesting ensures information stays with the user
- End-to-end encryption protects calls, messages, and data sharing from intrusions
- Regulatory alignment is woven into architecture rather than applied reactively
- Networking functions—such as secure messaging and card sharing—expand without compromising confidentiality
Real-World Implementation
Privacy-first solutions are beginning to address many of the pain points in today’s digital exchanges.
For Individuals:
- Privacy is enhanced without reducing usability or the convenience of mobile-native communication
- Caller ID protection and robust spam filtering secure personal identity layers
- Data sovereignty is strengthened with direct user control over what is shared, when, and with whom
- New forms of networking—like Connecto’s privacy-preserving card exchange—enable professional interaction without oversharing
For Businesses:
- Compliance readiness evolves as regulation becomes more demanding around identity data
- Streamlined identity management supports digital transformation with reduced risk
- IdentityAI architecture resists emerging threats such as synthetic IDs and deepfakes
- Scalable models allow adoption without large-scale disruption to existing enterprise systems
The Path Forward: Building Digital Trust
The next era of digital communication will be defined not by how much data can be collected but by how effectively trust can be established while keeping personal information hidden. Privacy-first networking, demonstrated by solutions like Connecto, lays the groundwork for systems where identity becomes the secure enabler rather than the point of compromise.
Cyberattacks today do more than disrupt organisations for days; when personal data is lost, they fundamentally reshape how users perceive and trust those organisations. The convergence of AI and user-controlled IAM will play a central role in rebuilding that trust, with adaptive intelligence monitoring sessions, distinguishing genuine users from automated intrusions, and mitigating risks dynamically. What emerges is not merely a new toolset but a deeper redefinition of digital trust itself.