The Hidden Cost of Identity Management: Why Financial Leaders Must Rethink Their Security Strategy
The data breach crisis in financial services has reached a tipping point. In 2024, the average cost of a breach in the financial sector hit $6.08 million, representing a 22% premium over other industries. But beyond these staggering numbers lies an even more troubling truth: most organisations are investing heavily in identity management solutions that deliver operational overhead with minimal customer value while missing the one element that truly matters-TRUST.
For CIOs and CISOs leading financial institutions today, it’s time for a fundamental shift in how we approach identity security.
The Operational Burden of Traditional Identity Management
Most financial institutions today deploy a complex web of identity management solutions: Identity and Access Management (IAM), Privileged Access Management (PAM), and Identity Governance and Administration (IGA). While each plays a role in the security ecosystem, they share a common characteristic—they’re primarily operational tools that consume resources without directly boosting customer confidence.
IAM manages user authentication and access controls across systems. It answers the question “who gets in?” by verifying identities and enforcing access policies. While essential for security hygiene, IAM requires constant maintenance, integration efforts with every new application, and significant administrative overhead.
PAM goes further by securing privileged accounts—those administrator credentials that hold the keys to your most sensitive systems. It adds session monitoring, credential vaulting, and password rotation to protect against insider threats. Yet PAM deployment is notoriously complex, requiring specialised security controls for high-risk environments.
IGA attempts to bring governance to the chaos by managing access rights, conducting periodic reviews, and ensuring compliance with regulations. Organisations report that time-consuming manual processes are the number one issue driving IGA investment, with over half finding that developing and maintaining custom connectors represents a significant burden.
The reality? These systems represent substantial operational investments. Survey findings show that traditional IGA tools often cannot adapt easily to new cloud applications, leading to extensive custom coding. Administrative overhead remains high, implementation timelines stretch on, and organisations find themselves constantly playing catch-up.
More critically, while these tools protect the institution’s perimeter, they do nothing to reassure customers that their data is safe when a breach occurs.
They’re invisible to customers, creating no competitive differentiation and building zero customer trust (NOT to be mistaken with zero trust policy).
Data Loss Prevention: The Only Segment That Touches Customers
Among identity management segments, Data Loss Prevention (DLP) stands alone as the solution that directly impacts customer perception. Unlike IAM, PAM, and IGA—which operate behind the scenes—DLP actively protects customer data from unauthorised access, misuse, and exfiltration.
DLP solutions monitor data in motion, at rest, and in use. They detect when sensitive information is being accessed inappropriately and can prevent data from leaving your organisation. Most importantly, when properly communicated, DLP demonstrates to customers that you’re actively protecting their information, not just controlling who can log in.
The benefits are clear. DLP helps maintain customer trust by safeguarding sensitive information and demonstrating a commitment to data protection. In an era where consumers are increasingly concerned about privacy, this visible protection is essential for building and maintaining customer loyalty.
Current DLP systems also have limitations. They cannot prevent data theft once systems are compromised. It cannot make stolen data unintelligible to attackers. And critically, it cannot turn the narrative after a breach from “we failed to protect you” to “your data remains secure even after the attack.”
The Real Business Problem: Lost Trust Equals Lost Revenue
Here’s what keeps financial executives awake at night: cyberattacks don’t just cost money in direct damages—they destroy the foundation of customer relationships.
Research shows that 75% of customers would stop shopping with a brand after a security breach. More than 60% would avoid a company entirely following an incident. After suffering a breach involving personal financial data, the average firm loses 1.1% of its market value and experiences a 3.2 percentage point drop in year-on-year sales growth.
Consider the ripple effects. Cisco’s 2017 research revealed that 38% of organisations experiencing breaches lost more than 20% of their revenue. Perhaps more damaging, 22% lost customers, with 40% seeing more than 20% of business slip away. Another 23% missed out on new business opportunities, with 42% losing 20% of prospective projects.
The financial sector experiences these impacts acutely. As Jerome Powell, Chair of the Federal Reserve, stated: “Cyberattacks are now the foremost risk to the global financial system, even more so than the lending and liquidity risks that led to the 2008 financial crisis”.
When customers trust you with their life savings, their mortgage, their retirement—that trust is everything. A breach shatters that relationship. Research on bank data breaches shows customers who had information compromised were significantly more likely to terminate their relationship with the bank in the six months following the event, even when fully compensated and suffering no monetary loss.
The lack of attribution magnifies this effect. When banks cannot clearly explain what happened or trace fraud to a specific party, customer churn increases dramatically. Uncertainty becomes a significant source of lost loyalty.
This isn’t just an IT issue—it’s a fundamental business problem that threatens long-term viability.
Introducing Cyber Resilience: Turning Bad News Into Reassurance
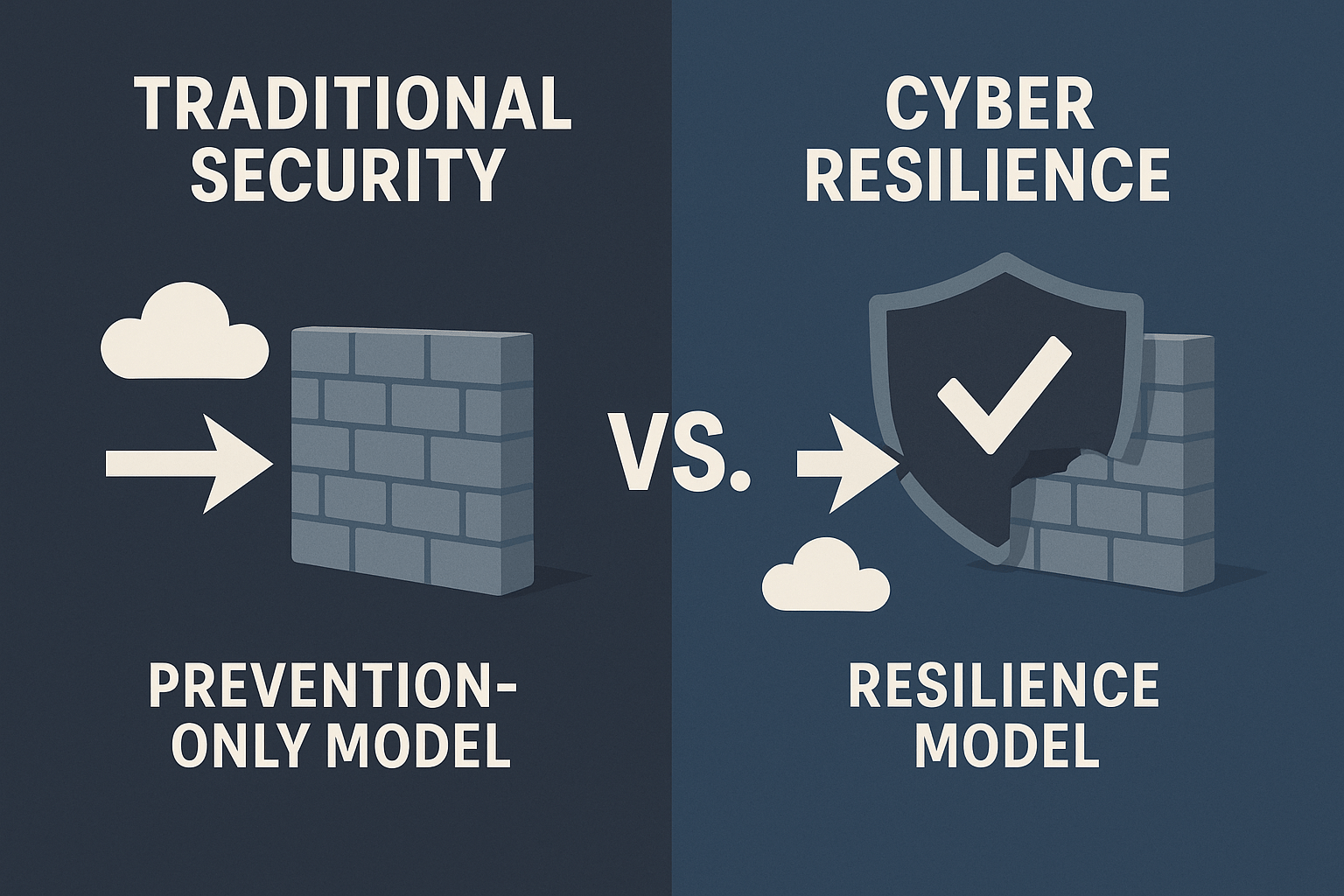
Traditional cybersecurity operates on a prevention model: build higher walls, add more locks, and monitor more carefully. But what happens when prevention fails? In today’s threat landscape, where attacks are inevitable, the question isn’t “if” but “when” you’ll face a breach.
This is where cyber resilience changes the game. Rather than only preventing attacks, cyber resilience assumes compromise and ensures your organisation can maintain operations and protect customer data even after an intrusion occurs.
For financial institutions, cyber resilience means the ability to adapt to disruptions caused by security incidents while maintaining continuous business operations. It’s the difference between telling customers “we were breached and your data may be compromised” versus “we were attacked, but your data remains protected.“
This mindset shift transforms how you communicate during a crisis. Instead of apologising for failure, you demonstrate strength. Instead of offering credit monitoring as consolation, you prove your architecture rendered stolen data useless to attackers.
The Australian financial regulators have recognised this imperative, developing cyber operational resilience frameworks and emphasising that no organisation is immune to attacks. The focus has shifted from preventing all breaches—an impossible task—to ensuring resilience when attacks occur.
The Keywix IdentityAI Solution: Unintelligible Data at Rest
This is where Keywix IdentityAI fundamentally changes the equation for financial institutions. Rather than simply managing who accesses data, Keywix ensures that data itself becomes unintelligible at rest through advanced encryption architecture.
Unintelligible data at rest means that even if attackers breach your perimeter, compromise credentials, and exfiltrate information, they cannot read or use what they’ve stolen. The data remains cryptographically secured in a format that renders it meaningless without the proper decryption keys.
Traditional encryption approaches encrypt data, but the keys often reside in systems that administrators can access. Keywix IdentityAI takes a different approach through its architecture, where encryption renders data truly unintelligible to unauthorised parties. This creates a defence layer that persists even after network security fails.
The customer value proposition is transformative. When you can tell customers that their data was encrypted in a way that makes it unusable to attackers—even after a breach—you’re not just managing a crisis, you’re demonstrating preparation and competence.
User-Controlled Identity: The Trust Multiplier
Beyond data protection, Keywix IdentityAI introduces another critical element: user-controlled identity management.
User-controlled identity puts customers in the driver’s seat of their own information. Rather than trusting institutions to protect credentials, customers maintain control through this architecture that prioritises security, privacy, and individual autonomy.
Research shows this approach addresses the fundamental trust deficit created by repeated breaches. When customers control their identity rather than merely trusting institutions to protect it, the power dynamic shifts. User-controlled identity concepts demonstrate that user control, privacy preservation, and enhanced security can coexist.
For financial institutions, this solves a critical problem: how do you rebuild trust after customers have learned—often repeatedly—that centralised data stores make attractive targets? User-controlled identity distributes risk while demonstrating respect for customer autonomy.
The operational benefits compound over time. User-controlled systems reduce the administrative burden of identity management. Customers perform their own identity verification and access management within defined policies, reducing help desk calls and provisioning delays.
Identity and access management that emphasises user control also improves regulatory compliance by providing detailed audit trails while giving customers the transparency and control regulators increasingly demand.
Why Financial Services Need This Now
The regulatory environment for financial institutions grows more demanding yearly. In the United States, financial institutions must report cyber incidents within 36 hours, with failure to comply bringing substantial fines and legal consequences. The Digital Operational Resilience Act (DORA) in Europe establishes even more stringent requirements.
Beyond compliance, competitive pressure intensifies. Fintech disruptors emphasise security and user experience as differentiators. Traditional institutions that cannot demonstrate both robust protection and customer-centric identity management risk losing market share to more nimble competitors.
The talent shortage compounds these challenges. Organisations struggle to find qualified cybersecurity professionals while operational overhead from traditional IAM, PAM, and IGA solutions continues to consume resources. Solutions that reduce administrative burden while improving security outcomes become strategic imperatives, not nice-to-have features.
Most importantly, the cost of inaction escalates. The average breach now costs $6.08 million in direct damages, but total losses from shareholder wealth destruction far exceed these figures. For the 75 initial attacks studied, total shareholder wealth loss amounted to $104 billion while identifiable direct costs totalled only $1.2 billion. The reputation costs dwarf the technical costs.
From Crisis to Confidence: Changing the Narrative
Imagine the next time your institution faces a security incident. Instead of the standard crisis playbook—apologising, offering credit monitoring, watching customer churn accelerate—you communicate differently.
“We detected and contained a sophisticated attack on our systems. While attackers gained unauthorised access, we want to assure you that your data was protected by our cyber-resilient architecture. All sensitive information was encrypted using unintelligible data at rest technology, rendering it useless to the attackers. Your user-controlled identity credentials remained secure, and no action is required on your part.”
This isn’t just better PR—it’s a fundamental truth enabled by the right architecture. You’re not spinning a disaster; you’re demonstrating that your security strategy worked exactly as designed.
The post-breach communication research is clear: transparency, speed, and accountability matter. But what if you could add a fourth element—reassurance through demonstrable protection? That’s the competitive advantage cyber resilience delivers.
Studies of reputation management after breaches show that companies demonstrating proactive security measures fare significantly better. The financial market reaction to cyberattacks is measurably worse when organisations cannot demonstrate adequate preparation.
With Keywix IdentityAI’s approach to unintelligible data and user-controlled identity, you transform the breach narrative from failure to validation. You demonstrate that your security investments protected customers even when prevention failed.
The ROI of Modern Identity Management
Forward-thinking financial institutions are realising significant returns from modern identity solutions. Organisations implementing identity-focused security measures can experience 50% fewer breaches than those without. Such identity architectures can reduce the average cost of a breach by nearly $1 million.
Beyond security incident reduction, operational benefits include help desk ticket reductions of up to 40% through self-service capabilities, 80% faster onboarding through automated provisioning, and 70% decreases in password reset requests.
Compliance becomes more manageable, with automated access reviews reducing certification time by up to 80% and audit preparation time declining by 50-70%. User experience improvements include average time savings of 15 minutes per day from single sign-on and 35% increases in employee satisfaction from mobile-friendly access.
But the true ROI comes from avoiding the catastrophic costs of lost customer trust. When you consider that successful cyberattacks cause substantial reputation costs with shareholder wealth losses far exceeding direct costs, investments in cyber-resilient identity architecture become strategic imperatives.
Your Strategic Imperatives as a Financial Leader
As CIO or CISO of a financial institution, you face three critical challenges: protecting customer data, maintaining operational efficiency, and building customer trust. Traditional identity management solutions address only the first two, and often at great operational expense.
The path forward requires embracing cyber resilience as a strategic pillar. This means:
First, recognising that IAM, PAM, and IGA are necessary but insufficient. They manage operational security without building customer confidence. Continue maintaining these systems for baseline protection, but don’t mistake them for competitive differentiators.
Second, acknowledging that DLP protects data in motion but cannot guarantee protection after exfiltration. You need architecture that renders stolen data useless.
Third, implementing unintelligible data at rest as a core principle. When attackers cannot read stolen information, breaches become costly nuisances rather than existential threats.
Fourth, giving customers control over their identity. User-controlled approaches align with regulatory trends, reduce operational overhead, and rebuild the trust that centralised breaches have eroded.
Fifth, preparing to change the post-breach narrative. With the right architecture, you transform “we failed to protect you” into “our cyber resilience protected your data despite the attack.“
Take Action: Transform Your Security Trajectory
The financial services industry stands at a crossroads. Cyberattacks will continue and likely intensify. Customers will continue demanding better protection. Regulators will continue tightening requirements. The question is whether your institution will lead or follow.
Keywix IdentityAI offers a clear path forward—one that combines unintelligible data at rest with user-controlled identity management to deliver true cyber resilience. This isn’t incremental improvement over existing IAM solutions; it’s a fundamental reimagining of how identity security can serve both institutional and customer needs.
The business case is compelling. Reduce the massive financial and reputational costs of breaches. Lower operational overhead through user-controlled identity approaches. Meet evolving regulatory requirements. Most importantly, build customer confidence in an era when trust has become your most valuable and vulnerable asset.
Don’t wait for the next breach to wish you had better architecture. The institutions that will thrive in the coming decade are those that view identity security not as an IT expense but as a strategic business advantage—one that protects customers even when prevention fails and turns potential crises into demonstrations of strength.
Discover how Keywix IdentityAI can transform your security trajectory. Schedule a demonstration to see how unintelligible data at rest and user-controlled identity management can make your financial institution truly cyber resilient. Visit Keywix.cloud to learn more and take the first step toward turning your next security challenge into a competitive advantage.



